New Year Special : Get 30% OFF + $999 Study Material FREE - SCHEDULE CALL
New Year Special : Get 30% OFF + $999 Study Material FREE - SCHEDULE CALL
It is predicted that worldwide, cyber crimes will cost $10.5 trillion annually by 2025. Enterprises experienced 130 security breaches per year, per organization, on average.
Cyberattacks are all around us in the digital world, increasing the need for a well-trained army of cyber warriors who can anticipate, identify, and limit the dangers. And as known demand brings competition, so you have to be among the best to land a job in cybersecurity. While possessing the required cybersecurity abilities is the first step, passing the interview is a completely different story. Cybersecurity interview questions can be tricky and based on any level of knowledge.
With expanding demand, there are exciting opportunities for anyone who is willing to reskill themselves for a career in cybersecurity with the online and expert-driven cybersecurity certification course online because the demand is much higher than the supply for cybersecurity professionals.
A sound knowledge of cyber security technical interview questions could lead you one step closer to becoming a successful cyber security engineer. We've put together this collection of the most relevant cybersecurity interview questions along with their answers to assist you in acing the test.
Cyber Security Training & Certification

By asking specific cybersecurity-related questions during interviews, employers can assess your knowledge of cybersecurity concepts and principles, your ability to identify and respond to any potential security threats, and your experience in implementing and maintaining security measures. Therefore, here is a list of 100 top cybersecurity interview questions you should definitely know about before you head out for your interview-
1. What are the elements of cybersecurity?
Ans:- Major elements of cybersecurity are:
Here is a list of top 10 in-demand cybersecurity skills for career success and beyond
2. Describe what encryption is?
Ans:- It is a method used to keep information safe from so-called adversaries. A message's sender and recipient can both read its contents thanks to cryptography.
3. What is the CIA?
Ans:- The Confidentiality, Integrity, and Availability (CIA) paradigm is a well-liked one for creating security policies. The CIA model is composed of three ideas:
4. What is Traceroute?
Ans:- A tool that displays the packet path is this one. It includes a list of every location the packet goes through. Most often, Traceroute is used when a packet fails to arrive at its destination. Traceroute is used to find the failure or to see where the connection falters.
5. Describe SSL
Ans:- Secure Sockets Layer is referred to as SSL. It refers to a technique that establishes secure communications between a web browser and a web server. To ensure data privacy, it is used to safeguard the information in digital payments and online transactions.
SSL is a way of keeping your information safe online. It helps keep your data secure from people who want to access it without permission.SSL is a way of keeping your information safe on the internet. It helps protect your data from people who are not allowed to see it.
6. Explain the brute force attack. How to prevent it?
Ans:- The best password or PIN can only be discovered through a process of trial and error. Hackers repeatedly attempt all possible credential combinations. Automated brute force attacks are common, when the programme attempts to log in using credentials automatically. Attacks using brute force can be avoided. As follows:
7. List the various OSI model layers.
Ans:- The seven OSI model layers are as follows:
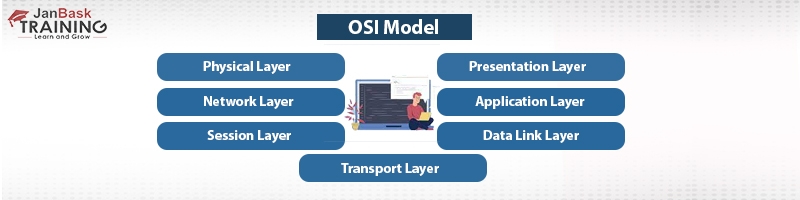
The OSI model - or Open Systems Interconnection model - is a standard for network communication between computers. It is a reference model that describes how network applications operate over the network, regardless of any differences between the networks themselves. The OSI model was developed by the International Organization for Standardization (ISO).
The OSI model is a reference model that forms the basis of computer networking. It provides a way of understanding how data is transmitted and exchanged between computers, regardless of the actual network components or protocols used. The OSI model consists of seven distinct layers which are divided into two main categories: the upper four layers (Application, Presentation, Session, and Transport) referred to as the “Application Layer” and the bottom three layers (Network, Data-Link, and Physical), referred to as the “Transport Layer”. Each layer of the OSI model has a specific function that it is responsible for.
8. What are black hat hackers?
Ans:- Black hat hackers refer to those that are skilled at getting past network security. These cybercriminals may produce malware for nefarious objectives such as monetary gain. They breach a secure network to alter, steal, or delete data in order to prevent authorized network users from using the network.
9. What do grey hat hackers do?
Ans:- This is one of the top cybersecurity interview questions. Grey hat hackers are computer hackers who occasionally transgress ethical standards but do not intend harm.
10. What is the MITM attack?
Ans:- An attack known as an MITM, or man-in-the-middle, occurs when an attacker eavesdrops on a conversation between two people. MITM's primary goal is to gain access to private data.
11. Describe a botnet.
Ans:- There are many internet-connected devices that are infected and under the control of malware, including servers, mobile devices, IoT devices, and PCs.
12. What does CSRF's acronym stand for?
Ans:- Cross-Site Request Forgery is referred to as CSRF. Cross-Site Request Forgery, also known as CSRF, is a type of attack that forces a user's browser to send malicious requests without their knowledge or consent. It is an exploitation of the trust that a website has in its users and can be used to gain unauthorized access to restricted resources and data.
13. Describe how symmetric and asymmetric encryption differ from one another.
Ans:- The same key is needed for encryption and decryption in symmetric encryption. Asymmetric encryption, on the other hand, requires unique keys for encryption and decryption.
14. Describe WAF
Ans:- WAF, or Web Application Firewall, is the acronym. By filtering and keeping track of incoming and outgoing internet traffic across web applications, WAF is used to safeguard the application.
15. Who are hackers?
Ans:- A hacker is a person who locates and uses a vulnerability in networks, mobile devices, or computer systems to obtain access. Hackers are skilled computer programmers who are familiar with computer security.
16. What role does DNS monitoring play?
Ans:- Young domains are susceptible to malware infection. To find malware, you must utilize DNS monitoring tools.
17. Describe SSH.
Ans:- Secure Shell or Secure Socket Shell is what SSH stands for. It is a collection of tools that gives network administrators safe access to networked data.
18. What are white box and black box testing?
Ans:- Software testing technique known as "black box testing" conceals the core architecture or source code.
White box testing implies a type of software testing where the tester is familiar with the internal workings of the application.
19. Describe the three-way handshake in TCP.
Ans:- It is a procedure carried out in a network to connect a local host and server. In order to use this approach, the client and server must first agree on synchronization and acknowledgment packets.
20. Define Exfiltration.
Ans:- An unauthorized transfer of data from a computer system is known as data exfiltration. Anyone with physical access to a computer can perform this communication manually.
21. Describe the meaning of penetration testing.
Ans:- It entails examining the target for exploitable flaws. It is used to supplement the web application firewall in terms of web security. This can be one of the important cybersecurity interview questions and answers.
22. What can be done to strengthen user authentication security?
Ans:- Users are required to provide their identification in order to be authenticated. The user's identity can be verified using the ID and Key. This is the best technique for the system to grant user authorization.
23. Identify the protocol that distributes data to all devices.
Ans:- A communication system called Internet Group Management Protocol, or IGMP, is utilized in game and video streaming. It makes packet sending easier for routers and other communication equipments.
24. What dangers come with using free WiFi?
Ans:- The security of public WiFi is a primary concern. Karma attacks, sniffers, war-driving, brute force attacks, etc., are examples of Wi-Fi attacks.
Data transferred through a network device, such as emails, passwords, browser history,and credit card information, may be recognized by public Wi-Fi.
25. Describe the primary distinction between RSA and Diffie-Hellman.
Ans:- While RSA is an algorithm that relies on two keys called the private key and the public key, Diffie-Hellman is a protocol that is used when exchanging keys between two parties.
26. Define forward secrecy.
Ans:- In the event that the long-term key is compromised, Forward Secrecy is a security feature that guarantees the integrity of the unique session key.
27. What does ECB and CBC's acronym stand for?
Ans:- ECB is for Electronic Codebook, and CBC stands for Cipher Block Chaining.
28. What is spyware?
Ans:- Knowledge of spyware is one of the most important cybersecurity interview questions as it is a threat to the safety of organizations. Malware called spyware seeks to steal information about a person or an organization. The computer system of the company could be harmed by this infection.
29. How would you define SRM?
Ans:- Security Reference Monitor, often known as SRM, offers procedures for computer drivers to grant access permissions to objects.
30. How would you define Authenticode?
Ans:- The publisher of Authenticode sign software can be found via the Authenticode technology. It enables users to confirm that the software is real and free of malicious code.
31. Explain how to secure a web server in number.
Ans:- To safeguard your web server, take the following actions:
32. What Does "Ethical Hacking" Mean?
Ans:-

Network security can be increased through the use of ethical hacking. Hackers strengthen computer systems and networks using this technique. Software tools are used by ethical hackers to weaken the system. Your knowledge of ethical hacking should be up to the mark if you want to excel at answering the cybersecurity interview questions. Here is a quick guide for beginners in ethical hacking.
33. What are MAC and IP addresses?
Ans:- Internet Protocol address is referred to as an IP address. On a computer network, an internet protocol address is utilized to uniquely recognize a computer or device, such as printers or storage discs.
Media Access Control address is referred to by the abbreviation MAC. At the physical layer of the network, MAC addresses can be used to uniquely identify network interfaces for communication.
34. Describe antivirus sensor technologies.
Ans:- Antivirus software is a program used to locate, stop, or get rid of infections from computers. They periodically inspect the system and tighten up the computer's security.
35. What exactly is a distributed denial-of-service (DDoS) attack?
Ans:- It is an attack in which numerous computers simultaneously target a server, website, or other network resources.
36. Describe the various session hijacking techniques.
Ans:- Different techniques for session hijacking include:
37. Describe honeypots.
Ans:- A honeypot is a fake computer system that keeps track of all user interactions, transactions, and actions.
38. What is Backdoor?
Ans:- It is a form of malware that can gain access to a system by getting beyond security measures.
39. What is the networking 80/20 rule?
Ans:- According to this rule, which is based on network traffic percentages, 80% of all network traffic should stay local and the other 20% should be forwarded to a permanent VPN.
40. What kinds of WEP cracking tools are there?
Ans:- Typical WEP cracking tools include:
41. Describe phishing.
Ans:- It is a method used to get other users to give over their username, password, and credit card information.
42. Define security testing.
Ans:- Security testing is a subset of software testing that assures software systems and applications are free from flaws, dangers, and threats that could result in significant financial loss.
43. List the hacking tools at your disposal.
Ans:- The list of helpful hacking tools is provided below.
44. What are penetration testing's drawbacks?
Ans:- The following are drawbacks of penetration testing:
45. What constitutes a physical threat?
Ans:- A potential cause of an incident that could lead to loss or physical damage to the computer systems is a physical danger.
46. What is a Trojan virus?
Ans:- Trojan is a type of software that hackers and online criminals use to infiltrate computers. Attackers in this instance utilize social engineering strategies to install the trojan on the machine. Knowledge of various types of viruses is essential for excelling in cybersecurity interview questions and answers session.
47. List security flaws in accordance with the Open Web Application Security Project.
Ans:- In accordance to the Open Web Application Security Project, there are the following security flaws:
48. Describe ARP Poisoning
Ans:- A sort of cyber-attack called ARP (Address Resolution Protocol) Poisoning is used to translate an IP address on a network device into a physical address. An ARP broadcast is sent over the network by the host, and the receiver machine replies with its physical address.
ARP poisoning involves delivering fictitious addresses to the switch so that it can link them to the IP address of a real computer on the network and divert traffic as a result.
49. Describe the steps that make up a TCP connection.
Ans:- A TCP connection follows the SYN-SYN ACK-ACK sequence.
50. What is Nmap, exactly?
Ans:- Nmap is a tool used for network discovery and security audits.
51. What kinds of cyberattacks are there?
Ans:- Two categories of cyberattacks exist: 1) Assaults on websites; 2) attacks on computer systems.
53. List some instances of system-based assaults (108)
Ans:- System-based assaults include, for example:
54. Define accidental hazards.
Ans:- They are accidental threats made by employees of the company. In these scenarios, an employee accidentally deletes any files or shares sensitive information with third parties or a business partner in violation of the company's policy.
54. Make a distinction between IDS and IPS.
Ans:- An intrusion is found using an intrusion detection system (IDS). When blocking the intrusion, the administrator needs to use caution. The Intrusion Prevention System (IPS) detects intrusions and takes action to stop them.
55. What benefits does cyber security offer?
Ans:- Know the cybersecurity advantages for enhancing your knowledge about cybersecurity interview questions:
Cyber Security Training & Certification

Want to know more about the applications and benefits of cybersecurity? Click here.
56. How do firewalls work?
Ans:- It is a network-specific security mechanism. Any system or network that monitors and regulates network traffic has a firewall installed on its perimeter. The main purpose of firewalls is to shield systems and networks against viruses, worms, and malware. Additionally, content filtering and remote access are prohibited by firewalls. Advanced knowledge of firewalls is vital for cyber security analyst interview questions.
57. By "data leaking," what do you mean?
Ans:- Unauthorized transmission of data to the public is known as data leaking. Email, optical discs, computers, and USB keys are all sources of data loss.
58. What is port scanning, exactly?
Ans:- It is a method for determining open ports and services accessible on a particular host. Hackers utilize the port scanning technique to gather data for their malicious purposes.
59. Describe a VPN.
Ans:- Virtual Private Network is a VPN. It is a technique for establishing secure and encrypted connections over networks. Data is shielded with this technique from tampering, spying, and censorship.
60. What do white hat hackers do?
Ans:- Penetration testing is a specialty of white hat hackers or security experts. They safeguard an organization's information system. These basic network security interview questions are essential for all the candidates to know.
61. How can a BIOS setup that is password-protected be reset?
Ans:- The BIOS password can be reset in a number of ways. Here are a few of them:
62. Describe the ARP and the way it operates.
Ans:- This protocol is used to identify the MAC address connected to an IPv4 address. This protocol serves as a bridge between the network and link layers of the OSI model.
63. What are SSL and TLS's key distinctions from one another?
Ans:- The primary distinction between these two is that SSL confirms the sender's identity. You can follow the person you are chatting with thanks to SSL. A secure channel between two clients is provided by TLS.
64. Describe 2FA for a public website, how should it be implemented?
Ans:- 2FA is an additional layer of security used to ensure that anyone attempting to access an online account are who they claim to be. A user will first input their login and password. Instead of receiving immediate access, they will be needed to submit additional information. Only once the user has presented valid identification to the authentication device will access be authorized.
65. What does XSS's complete name entail?
Ans:- Cross-site scripting is referred to as XSS.
66. What is hacking?
Ans:- Hacking is a popular term used for the process of identifying vulnerabilities in computer or private networks in order to take advantage of them and acquire access. Using password cracking techniques, for instance, to access a system.
Ethical hacking is a thriving career, learn more on how you can build a career in ethical hacking.
67. What is network sniffing?
Ans:- Data packets delivered over a network can be analyzed using a technology called network sniffing. Hardware or software with particular functionality can accomplish this. Sniffing is a technique for:
68. Describe the salting procedure. What purpose does salting serve?
Ans:- By employing special characters, a procedure known as salting allows passwords to be lengthened. It's crucial to understand the full salting operation in order to employ salting. Salting is used to protect passwords. Additionally, it stops attackers from scanning the system for recognised words.
To safeguard your password, for instance, Hash("QxLUF1bgIAdeQX") is appended to each and every password. The word for it is salt.
69. Can the SSL protocol provide enough network security?
Ans:- Although SSL authenticates the sender, it does not offer security once the data has been sent to the server. To guard the server from a data breach, server-side encryption and hashing are recommended.
70. Describe the weaknesses in network security.
Ans:- Vulnerabilities are the weak spot in software code that a threat actor could attack. They are most frequently discovered in software that is offered as a service, or SaaS.
71. What does residual risk mean? What are three strategies for managing risk?
Ans:- It is a threat that, when threats have been identified and eliminated, balances risk exposure.
There are three methods for managing risk:
72. In network security, what is an exploit?
Ans:- An exploit is a technique used by hackers to gain unauthorized access to data. It is included in malicious software.
73. Name a few typical cyber-attacks.
Ans:- The following are typical cyberattacks that hackers can use to harm networks:
Keep reading to know more about various types of cyber attacks.
74. Describe cross-site scripting as a notion.
Ans:- Cross-site scripting is a network security flaw that allows for the insertion of malicious scripts into websites. This attack happens when attackers let code injection from an unreliable source into a web application.
75. How can email messages be secured?
Ans:- To protect email, credit card data, and company data, use cypher algorithms.
76. What is Data Encryption? Why is it important in network security?
Ans:- With data encryption, the sender transforms the message into a code. It is only accessible to authorized users.
77. What is a remote desktop protocol?
Ans:- Microsoft created the Remote Desktop Protocol (RDP), which offers a GUI to link two machines across a network. While other devices must run RDP server software, the user utilizes RDP client software for this purpose. The remote management and access of virtual PCs, programs, and terminal servers are all made possible by this protocol.
78. Describe the idea of an IV in encryption.
Ans:- The initial vector, often known as IV, is a randomly chosen number that is used to guarantee that two pieces of identical text are encrypted with separate ciphertexts. This number is only used by the encryption application once per session.
79. Describe a few symmetric encryption algorithm examples.
Ans:- Here are a few symmetric encryption algorithm examples.
80. Describe a buffer overflow attack.
Ans:- A process that tries to write extra data to a fixed-length memory block is vulnerable to a buffer overflow attack.
81. What is impersonation?
Ans:- It is a method of giving a user account to an unidentified person.
82. What is a computer virus, exactly?
Ans:- A virus is a piece of malicious software that runs uninvited. Viruses can use computer resources such as memory and CPU time. The virus may occasionally introduce its own code and modify other computer applications in an effort to destroy the system. How it works:
83. Describe CryptoAPI.
Ans:- CryptoAPI is a group of encryption APIs that enable programmers to build a project over a secure network.
84. What do you mean by a worm?
Ans:- Malware that spreads from one computer to another is known as a worm.
85. List a few packet sniffing tools.
Ans:- Here are a few tools for packet sniffing-
86. List the several kinds of sniffing attacks.
Ans:- Numerous sniffer attacks include:
87. What Are Hacking Tools?
Ans:- Hacking Tools are computer tools and scripts that assist you in identifying and taking advantage of vulnerabilities in servers, networks, web applications, and computer systems. Such tools come in a variety and are sold on the market. While some of them are commercial solutions, others are open source.
88. List a few standard encryption tools.
Ans:- The following are some encryption tools:
89. Is it appropriate to send login information by email?
Ans:- It is improper to send login information over email since there is a high likelihood that the recipient will be the target of an email assault.
90. What is WEP cracking?
Ans:- It is a technique for hacking wireless networks' security. WEP cracking comes in two flavors: active cracking and passive cracking.
91. What exactly is a security audit?
Ans:- An internal examination of operating systems and applications for security issues is known as security auditing. Line-by-line analysis of the code can also be used to conduct an audit.
92. What is encryption at the nanoscale?
Ans:- Nano encryption is a field of study that offers computers strong security and guards against hackers.
93. Explain security scanning (number 89).
Ans:- Security scanning entails locating system and network vulnerabilities and then offering remedies for lowering these risks. Both manual and automated scanning can be done with this scanner.
94. What role does corporate penetration testing play?
Ans:- Here are two examples of typical penetration testing applications.
95. Describe the security threat.
Ans:- A security risk or a threat of cyber security attack is one that poses a possibility of stealing private information and endangering computer systems as well as an organization.
96. List some instances of non-physical threats.
Ans:- Here are a few instances of non-physical threat:
97. What Is SQL Injection?
Ans:- It is an attack that taints the database with malicious SQL statements. It aids you in exploiting design weaknesses in poorly constructed online apps to execute malicious SQL code through SQL statements. Attackers frequently escalate SQL injection attacks in order to carry out other attacks, such as denial-of-service attacks.
98. Establish a token of access.
Ans:- An access token is a credential that the system uses to determine whether or not to allow access to an API to a certain object.
99 . List the typical categories of non-physical threats.
Ans:- Various forms of non-physical threats are listed below:
100. Define hybrid attacks.
Ans:- Dictionary approach and brute force attack are combined in a hybrid attack. This technique modifies a dictionary word with symbols and numbers in order to break passwords.
Now that you are aware of the many concept-based cyber security engineer interview questions that could be asked, you can practice by consulting the provided solutions to each of these questions. Here, we looked at a wide range of interview questions on cyber security positions that were focused on ideas like networking, software and programming, operating systems and apps, cyberattacks, and cryptography.
Cyber Security is one of the most in-demand and thriving careers at present; there has been no better time to make the most of your cybersecurity skills. In case you are a beginner and want to build a career in cybersecurity, now is the time!
Check out JanBask Training’s Cyber Security Course if you want to learn more and develop a fascinating career. It includes instructor-led live training and real-life project experience. You will gain a thorough understanding, enabling you to become an expert on the subject and explore job opportunities like never before.
Do you have any queries about this post for us? If so, kindly include it in the article's comments area. Your questions will be promptly answered by our professionals! We hope that by using these cybersecurity interview questions, you'll succeed in your interview. Join our Cyber Security Masters Program right away to become an expert. All the best for your interview!
The JanBask Training Team includes certified professionals and expert writers dedicated to helping learners navigate their career journeys in QA, Cybersecurity, Salesforce, and more. Each article is carefully researched and reviewed to ensure quality and relevance.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Interviews