Introduction
We live more in our machines than in reality these days. Most of our data is on social networking sites or personal chatting platforms: our personal information, bank details, etc.
This has made our lives very prone to cyber threats. You may have already heard numerous incidents of cybercrimes wherein the personal information of individuals or companies was used to harm them.
This has led to a growing demand for cybersecurity professionals. As the name suggests, the main role of these professionals is to provide security to all the software, apps, APKs, etc.
Today, we shall go on to see how you can build a career in the domain of Cybersecurity with a detailed cybersecurity certification roadmap and guide you on the cybersecurity certification path and what all cyber security certifications are available.
Cybersecurity Certifications & Training Roadmap
Leverage your career with our cybersecurity certification roadmap. Walk us with the cybersecurity certification path and be a proud owner of one of the best cyber security certifications to help you stand out. Though a computer science degree is an excellent start, a Cyber Security certification that validates your skills is a huge green flag when it comes to landing your favorite job. Let us check the best certification for cyber security that is trending in the industry.
1. Certified Information Systems Security Professional – CISSP
CISSP is one of the advanced cybersecurity certifications in the field of cybersecurity. It is intended for those experts who are enthusiastic about seeking a vocation in data security. The ISC2 (International Information Systems Security Certification Consortium) offers the confirmation. Follow the cybersecurity certifications roadmap to know more about the cyber security certifications.
It is a vendor-oriented qualification, and it is comprehensively perceived for its significant level of measures. The experts with CISSP are leaders in their associations. They have the specialized aptitudes and master information expected to create, oversee, and manage security gauges, methods, and strategies inside their organizations. Most likely, this accreditation remains one of the exceptionally looked after by IT experts.
To win CISSP cyber security certifications, the applicants must have, at any rate, five years of working experience with Common Body of Knowledge spaces. An option is a four-year working involvement with at least two Common Body of Knowledge areas with higher education or another pertinent accreditation.
The CBK spaces of the International Information Systems Security Certification Consortium comprise of Security and Risk Management, Security Architecture and Engineering, Asset Security, Identity and Access Management, Security Operations, Security Assessment and Testing, Software Development Security, and Communications and Network Security.

2. Certified Information Systems Auditor – CISA
Another beneficial Cyber Security certification that is resume worthy. The CISA cybersecurity training programs teach how to manage audits and guarantee that IT assets are adequately protected.
Once you clear the CISA, you can assert your ability to apply a risk-based approach to planning, executing, and reporting on audit engagements and gain instant credibility in your interactions with internal stakeholders, regulators, external auditors, and customers.
This credential from the IT professional association ISACA helps demonstrate your expertise in assessing security vulnerabilities, designing and implementing controls, and reporting on compliance. It’s among the most recognized cyber security certifications chosen for the cyber security certification path for beginners and professionals.
You need at least five years of experience in IT or IS audit, control, security, or assurance. A two- or four-year degree can be substituted for one or two years of experience.

3. Systems Security Certified Practioner – SSCP
With this Cyber Security certification (ISC)², you can show employers that you have the necessary skills to design, implement, and monitor a secure IT infrastructure. The cyber security training classes make you an expert in access controls, risk identification and analysis, security administration, incident response, cryptography, and network, communications, systems, and application security.
The SSCP is designed for IT professionals working hands-on with an organization’s security systems or assets. This credential is appropriate for positions like:
Candidates for the SSCP need at least one year of paid work experience in one or more of the testing areas. This can also be satisfied with a bachelor’s or master’s degree in cybersecurity-related or cybersecurity training programs.

4. CompTIA Advanced Security Practioner – CASP+
The CASP+ cybersecurity certification path is designed for professionals who demonstrate advanced skills but want to continue working in technology. This certification path for cyber security covers advanced topics like enterprise security domain, risk analysis, software vulnerability, securing cloud and virtualization technologies, and cryptographic techniques.
The CASP+ can open up opportunities for advanced architecture, risk management, and enterprise security integration roles. There’s no formal prerequisite for taking the CASP+ exam. CompTIA recommends it only for experienced cybersecurity professionals with at least ten years of IT administration experience (including five years of broad hands-on experience with security).

5. GIAC Certified Incident Handler – GCIH
Earning the GCIH, one of the best certifications for cyber security validates your understanding of offensive operations, including standard attack techniques and vectors, and your ability to detect, respond, and defend against attacks. This cyber security certification path for beginners and professionals covers incident handling, computer crime investigation, hacker exploits, and hacker tools.
There are no formal prerequisites for taking the GCIH exam, though it’s a good idea to understand security principles, networking protocols, and the Windows Command Line.

6. Certified Ethical Hacker – CEH
Numerous associations have experienced the staggering impacts of programmers. Programmers are continually growing better approaches to assault the data frameworks and exploit the vulnerabilities of frameworks. To alleviate these assaults and dangers, organizations are proactively securing the data frameworks by utilizing the administrations of IT experts who have what it takes to thump programmers' hands.
These experts are referred to as 'White Hats' or 'White Hat Hackers.' The Red Hats use methods and aptitudes to recognize the framework vulnerabilities and passageways they can use to enter an association. The White Hats utilize similar strategies to forestall the Red Hat's undesirable access to data and system frameworks.
CEH is an intermediate-level cyber security certification affirmation regulated by the EC-Council (International Council of E-Commerce Consultants). This accreditation is profoundly prescribed for the experts hoping to explore a profession in moral hacking. You can Pass the CEH Exam in 30 Days with the right study plan and consistent effort.
The people with this accreditation have the information and abilities on hacking rehearses in various territories like examining systems, framework hacking, worms and infections, Trojans, sniffers, social designing, forswearing of-administration assaults, count, footprinting, and observation, session commandeering, SQL infusion, hacking web servers, cryptography, remote systems, and web applications, honeypots, dodging IDS, infiltration testing, and firewalls.

7. Certified Information Security Manager – CISM
CISM is a significant level cybersecurity training program and this certification is for the experts in the field of IT who are liable for creating, supervising, and overseeing data security frameworks in various endeavor-level applications. They are additionally answerable for building up the best security rehearses for associations. The Certified Information Security Manager accreditation was presented in 2003 and is regulated by the Information Systems Audit and Control Association – ISACA.
The objectives of ISACA are equipped with IT specialists who are keen on top-quality principles as far as control, security, and review of data frameworks. The endorsement is intended to address the issues of security experts in IT who are liable for big business-level security in the board capacities.
The CISM specialists have demonstrated and have propelled the abilities in program improvement and the board, security hazards the board, the occurrence of the executives and reaction, and administration. To hold this qualification, you should be prepared to consent to the Code of Professional Ethics of ISACA.
Also, you need to experience the broad test process. Notwithstanding, before you sit for the test, you should have at least five years of involvement in security, and you should likewise consent to agree to proceed with the instruction approach of ISACA.
The accreditation has been substantial for a long time. From that point onward, you will be required to recertify. You have to get, at any rate, 120 proceedings with proficient instruction credits over the three-year time of the authentication to empower you to recertify. Check out the cybersecurity certifications roadmap before choosing cyber security classes online.

8. CompTIA Security+
CompTIA Security+ is a vendor-neutral security accreditation. It is all around perceived and very much regarded in the business. The experts with these cyber security training classes are accepted to have higher specialized abilities, master information, and aptitudes in diverse security-related controls.
Even though the endorsement is a section-level capability, the people seeking the cybersecurity certificate programs must have a two-year involvement with organizing security. It is suggested that you seek after the CompTIA Network+ qualification before Security+
The competitors who accomplish the confirmation are specialists in different regions, including cryptography, danger the board, personality the executives, security chance ID and moderation, security foundation, security frameworks, and systems get to control. One reason why CompTIA Security+ is all around regarded in the business is that it is endorsed by the United States Department of Defense. What's more, it is likewise agreeable with the standard for ISO-17024.

9. SANS GIAC Security Essentials – GSEC
GSEC is one progressively incredible decision of a passage-level accreditation. This cybersecurity certification roadmap is offered by GIAC, and it is done by those experts who are trying to approve their comprehension of data security ideas and phrasing and their specialized mastery expected to take up hands-on security work jobs.
The people with the GSEC affirmation have the specialized abilities and information on different zones, for example, get to confirmation, perceiving and relieving general and remote assaults, secret word the board, cryptography basics, get to controls, DNS, IPv6, ICMP, arrange mapping, open key foundation, organize conventions, and Linux. Note that the testament is legitimate for a time of four years, after which it is important to restore it. To recertify, you have to collect an aggregate of 36 proceedings with proficient experience credits over the time of four years.

10. Offensive Security Certified Professional – OSCP
Even though it is fairly hard to get, OSCP is a cyber security certification that offers all of you the aptitudes you have to comprehend the infiltration testing procedure and life cycle. The Offensive Security Association offers it as a moral hacking qualification.
The up-and-comers seeking the endorsement are relied upon to sit for a 24-hour test that spotlights this present reality situation. Those who breeze through this assessment can recognize the vulnerabilities in security frameworks, bargain powerless PHD-scripps, perform controlled assaults, and compose basic Python/Bash scripts. Before you endeavor this test, you are required to experience the Penetration Testing instructional class, which Offensive Security offers. Take a detailed look at the cyber security certification roadmap before taking up cyber security classes online.

11. Certified Cloud Security Professional – CCSP
CCSP is one of the best cybersecurity training programs offered by the International Information Systems Security Certification Consortium (ISC2), and it is becoming very well known in the field of distributed computing frameworks. The accreditation is gone for the IT specialists with, at any rate, five years of important experience, including, at any rate, one year of cloud security work understanding.
The CCSP testament is perfect for the intermediate level and propelled level masters who are associated with IT design, data security, web and cloud security building, administration, IT reviewing, and hazard and consistency.

Below are cyber security certification facts at a glance:
|
Certification
|
Exam Fees
|
Experience Level
|
|
CompTIA Security+
|
$319
|
Entry
|
|
CISSP
|
$800
|
Expert
|
|
CISM
|
$800
|
Expert
|
Cyber Security Certifications do add a plus point to your profile. Professionals with the best cybersecurity certifications gain skills and help them to perform more quickly, easily, and confidently, which helps them to get a hike in their salary.
You can also read: CompTIA Security+ vs CEH certification.
Scope For A Cyber Security Professional
Since the world has now quickly moved towards an advanced environment, the dangers which pursue organizations additionally exist in the computerized structure. The information of organizations, media houses, and government associations are put away on their internet facilitating sites and individuals who are specialists in hacking can without much of a stretch bring this information.
In different segments, the obligations of lower and medium-level architects are being completed by processing frameworks that have brought down their interest. In any case, with regards to digital security, it is accepted that no other counterfeit or electronic security set-up can supplant the mastery of an individual.
For a similar explanation, the interest of digital security designers and supervisors has developed a specific level that straightforwardly counsel with the board individuals from the organizations. There are endless openings for experts with capability in digital security however the absence of individuals with the necessary information has still left numerous spots empty.
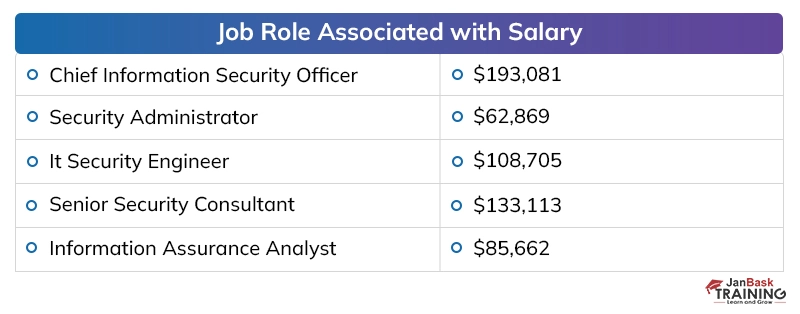
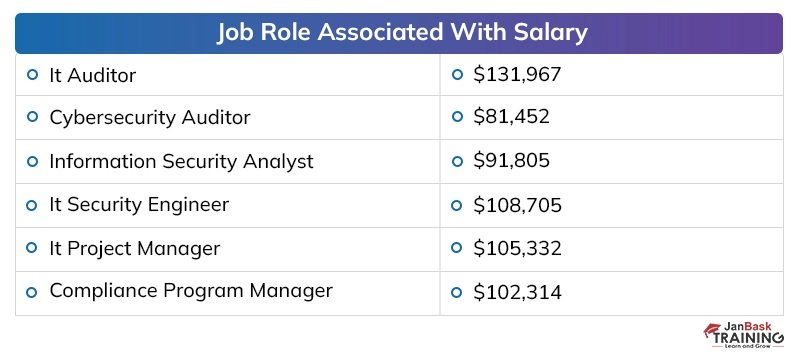
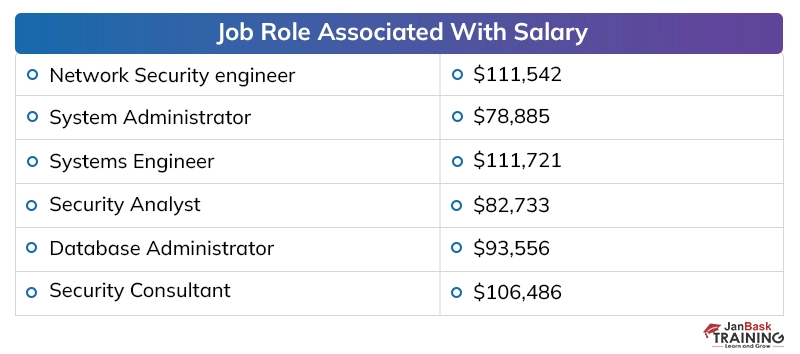
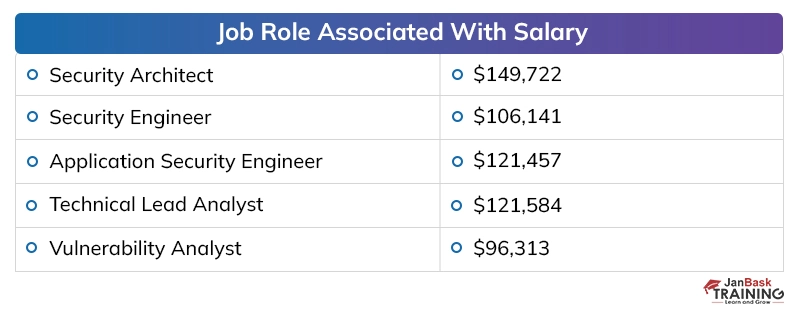
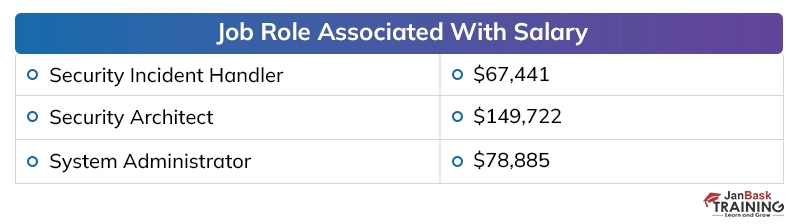
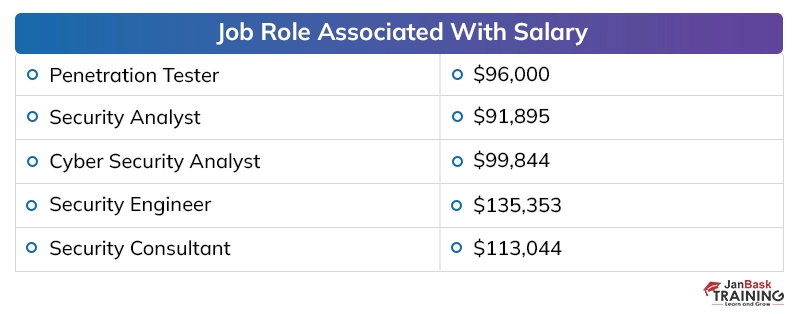
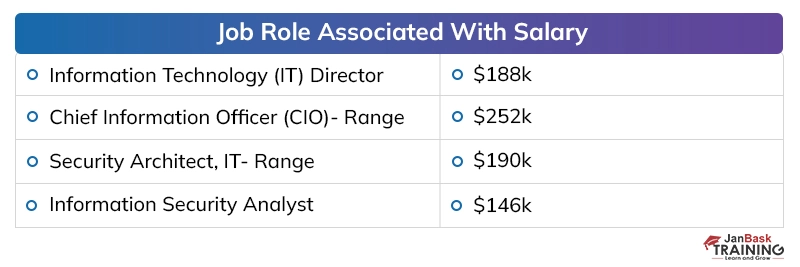
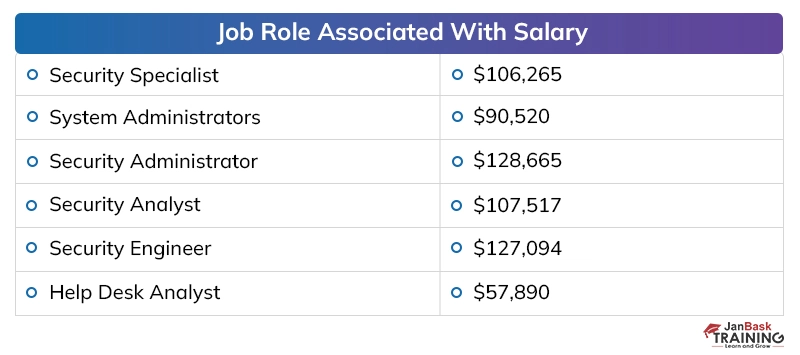
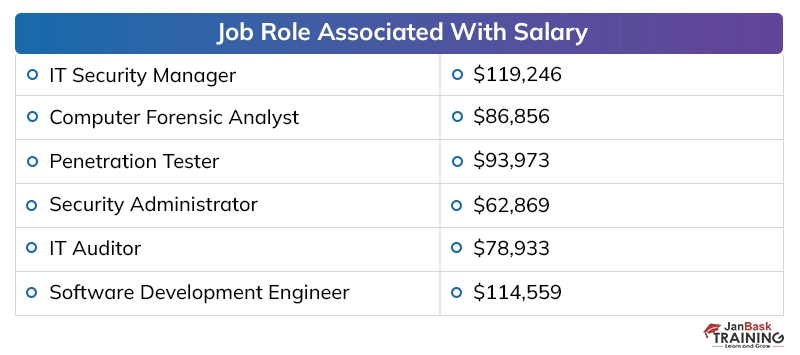
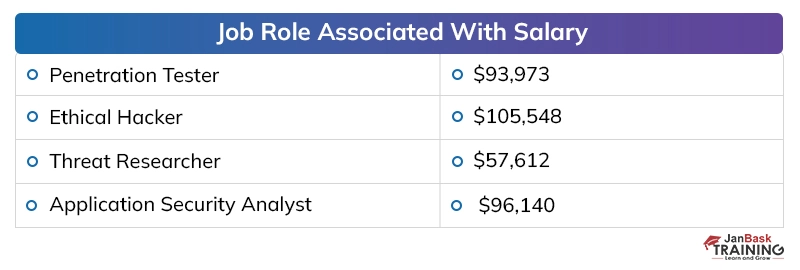
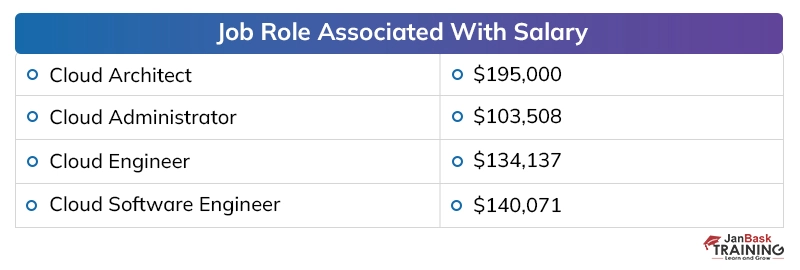
Discussing the payouts of digital security specialists in presumed firms, the yearly pay offered to a digital security proficient, at the beginning, periods, is around 40,000 to 50,000 dollars instead of the 2 to 4 million dollars for every annum bundle of building graduates in different fragments. The area has seen around 25 to 35 % ascend in the bundle plots over the most recent couple of long periods of digitization, which has made experienced individuals end up with a yearly pay of 20 to 40 million.
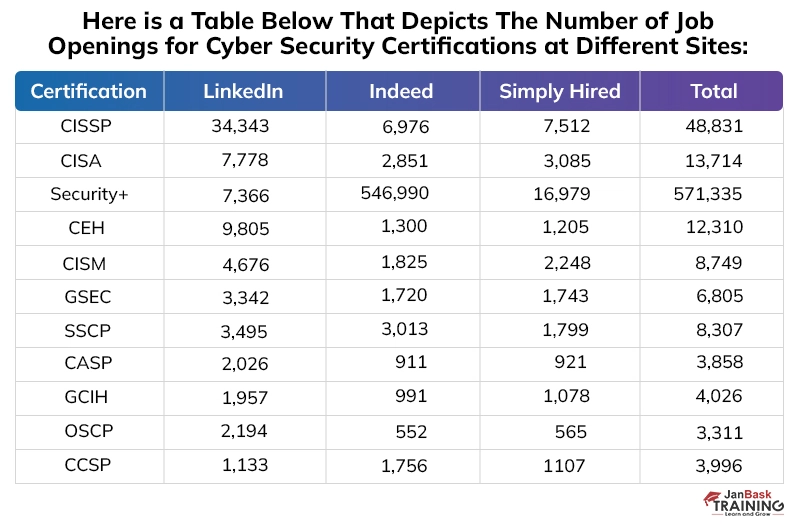
Here is a table below that depicts the number of job openings for cyber security certifications at different sites:

Cyber Security Salary
Let me just rapidly stress that the pay rates given underneath are simply estimations that can change at some random point in time. They ought to be utilized as a source of perspective, as opposed to a chilly, undeniable reality.

Entry-Level Salary
We should start by discussing the passage level cybersecurity compensation. As I've referenced before on in the article, the apprentice cybersecurity compensation relies upon a couple of various factors – these factors can impact the number to be both a lot littler and a lot greater, so remember that.
Even though it's extremely hard to locate a steady, explicit number to reference,
Businessinsider.com states that the normal cybersecurity spins around $84,000 every year point. This would like to turn out to be roughly $7000 every month!
Truly, remembering everything, this ends up being an astounding compensation! These estimations are situated in the US, where the normal month to month pay is around $3700 (as of composing this article). At the point when you think about this reality, the apprentice cybersecurity pay appears to be considerably progressively magnificent.
Junior Salary
As expressed before, the cybersecurity analysts or experts are compensated well, once they have some experience in the field. Therefore, the compensation of the junior level employees is fairly good.
As indicated by the site, junior cybersecurity investigators should make around $88,800 every year or $7402 every month. This bodes well, particularly when you contrast this lesser cybersecurity compensation with the novice one.
Read: Top 10 Ethical Hacking Tools
Senior Salary
As indicated by ZipRecruiter, a senior cybersecurity investigator can hope to make around $118,600 every year. This turns out to be a stunning $9,889 every month!
That an immense bounce from the normal pay of the lesser gathering! With this data, it would bode well to believe that the senior data investigator's necessities are a lot higher when contrasted with those of a lesser one.
Skills that you Need to Become Expert in Ethical Hacking
Initially, you'll need some basic work propensities, including the capacity to work systematically (and in a meticulous way). The accompanying capacities additionally prove to be handy:
- Eagerness to delve into specialized inquiries and inspect them from all sides.
- Enthusiasm and a high level of versatility.
- Strong systematic and indicative aptitudes.
- A current comprehension of normal web vulnerabilities.
- Maintaining mindfulness and information on contemporary principles, practices, techniques, and strategies.

Soft Skills
That is notwithstanding the previously mentioned delicate abilities; recall, security experts frequently need to convey convoluted subjects to individuals who probably won't have a lot of a specialized foundation, (for example, C-suite administrators). Given that, acing coming up next is normally a prerequisite for moving to further developed situations on the cybersecurity stepping stool:
- Excellent introduction and correspondence abilities to adequately speak with the board and clients.
- Ability to plainly explain complex ideas (both composed and verbally).
- Ability, comprehension, and utilization of undivided attention aptitudes (particularly with clients!).
From a cybersecurity viewpoint, delicate abilities will likewise enable you to recognize instances of and clarify, social building, which is an inescapable issue inside the security network. You can put a wide range of equipment and programming safety efforts set up, however, programmers can, in any case, utilize the social building to persuade clueless workers to give them passwords, certifications, and access to something else secure frameworks.
Technical Skills
Which specialized abilities do cybersecurity aces need? That question is somewhat trickier to reply to, as there are many sub-trains inside the cybersecurity field. That being stated, numerous such employments share a typically specialized establishment.
First off, tech experts ought to comprehend the design, organization, and the board of working frameworks (different Linux distros, Windows, and so on.), systems administration, and virtualization programming. As such, become more acquainted with—and love—things like firewalls and system load balancers. That is notwithstanding broad programming/programming advancement ideas and programming investigation aptitudes.
There's additionally the need to comprehend the more typical programming dialects, including Java, C/C++, disassemblers, low-level computing construct, and scripting dialects (PHP, Python, Perl, or shell).
1. Numerous businesses request to see your certifications as a prerequisite for work, and it's anything but difficult to perceive any reason why. In an ongoing review, the International Information System Security Certification Consortium (ISC)?
2. Noticed that a degree and confirmation were regularly a central point in employing. "Cybersecurity accreditations are basic to demonstrate the degree of information on cybersecurity proficient. Be that as it may, they ought to never alone be the main reference," Joseph Carson, the central security researcher at security merchant Thycotic, told Dice in an email.
“Signup Now to master your skills with our Cyber Security online training ”
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
Conclusion
The cybersecurity field has got great job potential. If you can game up and enter into this profession, it will be great for you. We all know that digitization is only going to increase with the coming years.
This pattern makes it very obvious that there will always be great jobs and great salaries in the field. Pull-up your socks, gain those cybersecurity skills, get cybersecurity certifications and enter the profession where your demand is way more than your competitors. Hurry up!
Read: How to Pass the CEH Exam in 30 Days: Pass on Your First Try
FAQs
Q1. Is a Cybersecurity Certification Worth It?
Ans. Yes, getting an industry-recognized cybersecurity certification is worth the investment. Certifications validate your skills and expertise in the domain, enhance your credibility, increase earning potential, open up new career opportunities, and allow you to stay updated on the latest best practices. Top certifications like CISM, CISSP, CEH, and Security+ demonstrate your commitment.
Q2. How Long Does It Take to Get Certified in Cybersecurity?
Ans. It typically takes 2-6 months of dedicated preparation to get certified in cybersecurity, depending on prior experience. Vendor-neutral certifications like CompTIA Security+ or EC-Council CEH require relatively less prep time compared to CISSP or CISM, which need extensive study across domains. A structured certification training program helps expedite preparation.
Q3. Does Cybersecurity Require Coding?
Ans. No, coding skills are not mandatory for many cybersecurity roles, especially on the governance, risk management, audit and analyst side. However, for careers like ethical hacking, malware analysis, forensics, security tool development, and engineering - programming knowledge is required and preferred. Overall, coding expands opportunities.
Q4. What Skills Do I Need for Cybersecurity?
Ans. Key skills needed are analytical thinking, attention to detail, problem-solving, technical acumen, communication, and passion for continuous learning. Domain expertise in OS, networking, risk, and compliance is vital. Being adaptable, ethical, and having investigative curiosity also helps me succeed as a cybersecurity professional.
Q5. What Are the Major Cybersecurity Threats?
Ans. Top cyber threats are phishing, ransomware, DDoS attacks, insider threats, unsecured IoT devices, third-party breaches, unpatched software vulnerabilities, insecure APIs, cloud misconfigurations, brute force attacks, and DNS spoofing. Staying vigilant and keeping systems patched and secured is essential to mitigate risks.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
2 days 10 Jan 2026
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
2 days 10 Jan 2026
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
7 days 15 Jan 2026
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
1 day 09 Jan 2026
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 09 Jan 2026
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 16 Jan 2026
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
2 days 10 Jan 2026
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
2 days 10 Jan 2026
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 09 Jan 2026
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
9 days 17 Jan 2026
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
1 day 09 Jan 2026
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
2 days 10 Jan 2026