Introduction
Ethical hackers are in soaring demand, and that's hardly surprising—with cyber crime costs ballooning year after year. According to Cybersecurity Ventures, global cybercrime damages are projected to hit US $10.5 trillion by 2025, nearly doubling from around $3 trillion in 2015.
Organizations are eager to hire skilled ethical hackers—and they’re willing to pay well for the talent. In the U.S., typical salaries range from approximately $90,000 to $140,000, with top professionals earning up to $160,000 or more depending on their experience and certifications. Globally, the median salary for ethical hackers in 2025 hovers around $143,300, with most professionals earning between $98,000 and $180,000.
So it's no wonder that ethical hacking has become an appealing and lucrative career path for many people worldwide.
In this ethical hacker tutorials guide blog, you will be learning beginner’s concepts that are required for you to get started as an ethical hacker. We’ll be discussing the following topics-
- Overview on Cybersecurity, cryptography, and cryptanalysis
- Stages of ethical hacking & complete ethical hacker tutorials
- Ethical Hacking basics: What tools can you use to perform ethical hacking?
- What techniques can you use to perform ethical hacking?
- What you can do legally? What you cannot do legally?
- What is an ethical hacking course? And, why is taking an Ethical hacking course necessary?
Before we go in-depth on an ethical hacking tutorial, first let’s understand the concept of cybersecurity and cryptography.
Cybersecurity and Cryptography
The first board is cryptography and the second is cybersecurity.

Cybersecurity is tied in with guaranteeing your clients don't do inept things, it is an IT job and each organization now needs them.
Cryptography is the specialty of figuring content into a mixed-up design. In case your information falls into an inappropriate hand, you can remain calm as long as it is all around scrambled. Just the individual with the decoding key will have the option to see the information. An ethical hacker is increasingly inspired by the working of algorithms that let him decipher the information without the key. This is called cryptanalysis.
Cryptanalysis is the investigation of breaking down data frameworks so as to contemplate the concealed parts of the systems. Cryptanalysis is utilized to breach cryptographic security systems and access the substance of encoded messages, regardless of whether the cryptographic key is unknown. Approaches like Brute force, Dictionary attacks, and Rainbow table attacks have all originated from cryptanalysis.
You should not be planning new cryptographic calculations except if you are a scholastic, or working in a group with scholastics.
We are currently living in an area of digitization. Whether it is a booking of a hotel room or ordering some dinner or even booking a cab, we are constantly using the internet and inherently generating data. This data is generally stored on the cloud which is basically a huge data server or data center that you can access online. Also, an array of devices is used to access this data.
“Russian hackers are the fastest.”
“300,000 new malware is created every day.”
Read: How to Become Cyber Security Expert
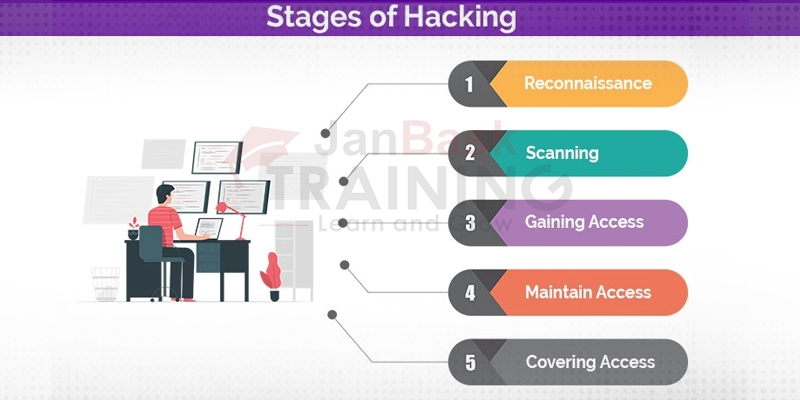
Ethical Hacker Tutorials Guide for Beginners: Stages of Hacking

Level 1 - Reconnaissance: It is the demonstration of get-together of data identified with insight and starter information of your objective to get ready for attack in a superior manner. It can be done either effectively or passively (Network, IP address, DNS records). Hackers will invest the greater part of the energy at this level.
Level 2 - Scanning: It is an earlier stage to propelling the attack. At this level, we examine open ports, services and so forth. The tools utilized by the hacker during the checking would be port scanners, sweepers, dialers, and vulnerability scanners.
Level 3 - Gaining Access: The outline of the targeted system will be prepared from levels 1 and 2. At this level, we obtain entrance for the targeted system by getting to one or more network devices to remove the data from the target.
Level 4 - Maintain Access: At this level, the hacker will be in stealth mode to abstain from getting captured while working in the host environment. When the programmer obtains entrance, he lays the way for future assaults and violations by making the objective solidified. Hacker likewise verifies the way by some other detour getting to with rootkits, secondary passages, and Trojans.
Level 5 - Covering Tracks: At this level, the hacker covers his track so as to get captured and recognized by the digital workforce or cyber personnel. He evacuates proof of hacking to keep away from legitimate activities. Hacker evacuates all log files, IDS (tunneling conventions, steganography, modify log records)
These are the different levels discussed in most of the ethical hacker tutorials.
Do you know, “Multi-factor authentication and encryption are the biggest hacker obstacles.”
Cyber Threats
A). Physical Threats
Under the hacking tutorial, Physical threats are further divided into three categories.
- Internal e.g. hardware fire, faulty power supply, internal hardware failures, etc.
- External e.g. floods, fires, earthquakes, etc.
- Human e.g. vandalism, arson, accidental errors, etc.
B). Non-Physical Threats
Non-physical threats include every threat that has no physical manifestation. They are also known as logical threats. Below is a picture of the most common non-physical threats:

What Tools can you use to Perform Ethical Hacking?
Below is the list of tools used in hacking as per most of the ethical hacker tutorials guide:
|
Tool
|
Description
|
|
Netsparker
|
It is a web application security scanner which automatically distinguishes SQL, XSS and different loops in web applications and administrations
|
|
Probe.ly
|
It constantly checks the web applications for loops
|
|
Acunetix
|
It is completely robotized hacking solution which imitates ethical programmer to keep in front of malevolent attacks
|
|
Burp Suite
|
It is a Security Testing tool for web applications
|
|
Aircrack
|
It is utilized to crack wireless communications and controlled by WPA 2 and WEP WPA
|
|
Ettercap
|
It helps in the analyzation of network and host examination of dynamic and passives modes devices
|
|
GFI LanGuard
|
It tends to be as a "Virtual Consultant" which outputs network for vulnerabilities
|
|
Angry IP Scanner
|
It is utilized to check ports and IP addresses as it is a cross-stage and open-source device
|
|
QualysGuard
|
It constructs security to digital transformations. It additionally helps in recognizing cloud system vulnerabilities
|
|
WebInspect
|
It is a dynamic application security testing tool
|
|
Savvius
|
It recognizes issues and reduces security risk along with deep analysis given through Omnipeek
|
|
Hashcat
|
It is a password cracking device for ethical programmers
|
|
IKECrack
|
It is a verification cracking device
|
|
SQLMap
|
It distinguishes and exploits the SQL injection loopholes in the framework
|
|
Medusa
|
It is utilized to crack the password. It is expedient and the best online ethical hacking tool
|
|
NetStumbler
|
It is the tool to recognize wireless router networks for Windows operating system
|
|
Cain and Abel
|
It is a password recovery tool for Microsoft operating system
|
|
RainbowCrack
|
It is the password hacking tool utilized by the majority of the ethical programmers
|
|
L0phtCrack
|
It is the tool used to recoup and review the password for the systems
|
|
IronWASP
|
It is fortware accessible online for free for ethical hacking and it is open source
|
“Cybercriminals could view your stored data on the phone, including identity and financial information.”
What Techniques can you use to Perform Ethical Hacking?
When you check through the hacking tutorial, you find hackers utilize various sorts of procedures. The recognizable ones are referenced underneath.
- Password Cracking - Recovering passwords transmitted by means of PCs
- Vulnerability Scanner - Network checking for the known shortcoming
- Spoofing Attack – It involves bogus websites, to be trusted by clients for information breaching
- Packet Sniffer - Apps that distinguish data packets for data or passwords seen in travel by means of networks
- Trojan Horse - It goes about as indirect access for an intruder to access the system
- Rootkit - It gives a set of projects to have authority over OS with genuine administrators
- Keyloggers - Used to record every keystroke in the machine for gathering later
- Viruses - These are self-imitating executable programs without anyone else into various documents
So, these are the techniques generally mentioned in the ethical hacker tutorials. Next, we will learn how to do hacking in a legal way and how to go for learning to hack for beginners.
Learning to Hack for Beginners: What you can do Legally?
Laws change from place to place. You should be aware of what is allowed and what is not allowed. It comes under the hacking basics. Various tools that are required for white hat hacking might be illegal to use. You should contact local law enforcement agencies before installing hacking tools because Governments are keeping eagle eyes against cybercrimes and are fully supporting cyber-laws and are more serious about punishment for cybercrime.
Do you know what cybercrime is?
Cybercrime is characterized as wrongdoing wherein a PC framework is utilized as a device for carrying out the offense. Cybercrime incorporates getting to your own data, private information or handicapping your gadget. Underneath references are barely any classification-based cybercrimes.
Classifications:
- Property
- Individual
- Government
Kinds of Cyber Crimes:
- Botnets
- DDoS Attacks
- Identity Theft
- Social Engineering
- Cyberstalking
- Phishing Attacks
- PUPs
- Online Scams
- Illegal Content
- Exploit Kits
What you cannot do Legally as per the Ethical Hacker Tutorials?
Accessing computers without permission of the owner is illegal. Other illegal actions include-
- Installing worms or viruses
- Denial of Services attacks
- Denying users access to network resources
Be careful about your actions and do not prevent customers from doing their jobs. Following are the ways you can avoid a legal action as per the hacking tutorial-
- Using a contract is a good way to perform risky ethical hacking
- Getting everything in writing will be useful in court if required
- Always have an attorney over your contract before reading or signing it
- Get express (written, ideally) authorization to endeavor to infiltrate a company’s framework
- Be aware of all the organization's rules and policies
- Advise the organization all things considered and vulnerabilities found
- Leave the system in the manner it was discovered, that is, don't make any shortcomings that could be exploited in the future
- Keep a written record of what is done on the system
- Try not to disregard the laws of a nation by, for instance, accomplishing something that ruptures copyrights, licensed innovation, protection laws, etc.
“Know that no bank or online payment system will ever ask you for your login credentials, social security number, or credit card numbers by means of email.”
So, these are the terms you can do and cannot do in hacking and that’s it on beginners guide to hacking. With the increasing number of cyber threats, the demand for ethical hackers is rapidly increasing. Below are the insights on the global demand of ethical hackers.
Worldwide Ethical Hacker Job Demands
Developing at a rate that is outpacing all other IT segments, cybersecurity has emerged as one of the highest growing in the entire decade. In the last five years, the list of cybersecurity jobs has increased by 75% as per the analysis of the Bureau of Labor Statistics.
The Industry watchdog Cybersecurity Ventures predicts, “There will be 3.5 million unfilled cybersecurity jobs worldwide this year.”
A recent search for “ethical hacker” jobs on LinkedIn reveals several thousand jobs at a range of reputed organizations like Fidelity Investments, Microsoft, TikTok, Booz Allen Hamilton, Tesla, the Federal Reserve Bank, the U.S. Department of Defense to name a few.
Amid the ongoing wave of cybercrime, it is common to see why demand is so high for ethical hackers.
But before you begin your journey with an ethical hacker training course and required skill set, let’s first understand what exactly an ethical hacker does in their day to day activity with the beginners guide to hacking.
Ethical Hacker Tutorials Guide: Ethical Hacker Roles & Responsibilities
There is a general misconception that an ethical hacker is only responsible for penetration testing of systems and applications. Well, that’s not true, and an ethical hacker does a lot more than that.
- Define and organized system and network resources into different sections
- Monitor system and network resources for potential threats
- Identify potential threats to the systems or resources
- Create strategies to deal with potential issues
- Implement solutions to minimize the consequences of an attack
- Do testing on target resources like web resources, hardware, and software
- Keep all systems updated with the latest vendor patches and service packs
- Research to develop new strategies to count new hacking methodologies and mitigate the possible threats
- Make security-related policies and ensure that the policies are enforced correctly
Well, you might get confused with different tasks and duties when it comes to the Cybersecurity career path in general or ethical hacking in particular. However, the exact role depends upon the level of expertise a professional holds.
Here, checking through ethical hacker tutorials and training courses can help you prepare for the future. Before you deep dive into the courses available, first, we will take a look at the salary range of an ethical hacker.
Salaries of an Ethical Hacker
As a career, ethical hacking continues to be very rewarding. In recent years, salary trends have shown steady growth as organizations strengthen their cybersecurity posture. According to updated reports, ethical hackers and penetration testers are among the top-earning professionals in IT security.
Here are some of the latest ethical hacker certification salary snapshots from popular websites (2025 data):
-
The average salary of a penetration tester is $121,000 on ZipRecruiter.com
-
The average salary of a penetration and vulnerability tester is $108,000 on CyberSeek.org
-
The average salary of an ethical hacker is $103,866 on Salary.com
-
The average salary of a Certified Ethical Hacker (CEH) is $94,000 on Payscale.com
Considering these trends, it’s clear that ethical hackers are highly paid and remain in huge demand globally. With salaries ranging between $90,000 and $140,000 (and even higher for senior roles), this career path is becoming more attractive for fresh graduates and IT professionals alike.
Do you know what the average salary of Cybersecurity professionals?
Prerequisite Needed: Educational Qualification & Skills Required to Become an Ethical Hacker
The first requirement to become an ethical hacker is a Bachelor’s degree (BSc, BTech, BE, BCA) in IT or Computer Science. Candidates having an advanced diploma in network security or relevant tech segment can also go for the ethical hacking career. A Cybersecurity certification from a reputed institution can enhance your chance of getting hired by renowned brands in the IT sector.
- Basic computer skills (not just MS Word but using the command line, editing the registry, and setting up a network
- Networking skills (for example, understanding routers and switches, internet protocols, and advanced TCP/IP) are essential for a programmer to maintain an advanced network system given at any point of the process.
- A programmer should also have an expert knowledge of the nature and functionalities of operating systems. There are only two Operating systems that programmers must learn in depth – Windows and Linux skills (these are non-negotiable)
- A programmer must get a grip over the Hacker tools (for example, Wireshark, TcpDump, and Kali Linux) used for the purpose of hacking. Ethical hackers generally use the same tools as black-hat hackers use.
- Having some knowledge of SQL injection is another major skills. It is a vulnerability that enables programmes to access data that are only accessible by an application.
- Virtualization
- Security concepts and technologies (such as SSL, IDS, and firewalls)
- Wireless technologies
- Scripting (for example, Perl, BASH, and Windows PowerShell)
- Database skills (starting with SQL)
- Web programming and applications (how hackers target them)
- Digital forensics
- Cryptography (encryption)
- Reverse engineering
These are the technical expertise an ethical hacker needs to have. Just going through some ethical hacker tutorials and getting certified is not enough. If you are just starting out and want to understand hacking for beginners. You can understand this way, hacking is actually a service that is done by individuals who are technically curious and extremely passionate. In addition, an ethical hacker also requires a set of soft skills like Confidence, optimism, patience, perseverance, good problem-solving skills along with good communication and presentation skills to excel in the explicitly booming field of cybersecurity.
Ethical Hacker Roadmap: Where to Start?
Patience is another important skill you need to cultivate if you want to begin with the ethical hacking for beginners and embark on a career as an ethical hacker. There is immense potential to achieve both in a short span of time if you make efforts with the right approach! To help you achieve that position, here is the stepwise process on Ethical Hacking career path:
Complete Your Graduation
Ethical hacking is an advanced career position where you need to hold extensive experience in network security. Although a significant part of Cybersecurity training or ethical hacking for beginners and experts is through on-the-job training and certification, to start the career path, you should have a strong understanding of computer components and computer science.
You can gain this knowledge while doing your graduation. Also, opt for the universities that have strong computer science programs and search classes that specialize in ethical hacking and security.
Work on Technical Knowledge & Skills
Tenderfoots who need experience with the field, it's ideal to begin from the nuts and bolts. Rather than adapting legitimately how to hack, you need to start to investigate themes, for example,
- Computer networks
- Network ports
- Firewalls
- Computer network protocols like IP addresses
- HTTP, FTP, DNS, SMTP
You can likewise begin to adapt progressive alternatives like Linux. This enables you to pick up information on everything fundamental in the field of hacking. The more you find out about nuts and bolts, the simpler it is to discover vulnerabilities and device exploits. When you create an essential comprehension of the fundamental ideas, you will be in a situation to comprehend different hacking systems that are presently in practice.
Be a Code Geek
If you need to become extraordinary at hacking, you need to master programming. This is a section you can't skip. Although, there are a ton of tools and projects that make everything simple for you, however, you likewise need to know how to program.
You're required to have knowledge in dialects like:
- HTML
- PHP
- JavaScript
- Other applicable dialects
This will lead you to a superior situation to make sense of how they work and to figure out the foundation of every language. Obviously, you can be extraordinary at hacking without realizing how to program by any stretch of the imagination! Be that as it may, learning it makes it path simpler for you to succeed.
Everybody can ace ethical hacking and hack like an expert when you take it from the basics and construct a strong establishment.
In this way, so as to turn into a programmer you will require
- A zeal to learn
- Perseverance
- Great asset information
- Hard and committed work
Try not to concentrate on to what extent it takes for it to ace hacking, simply trust the advancement.
“A gang of teenage hackers broke into computer systems throughout the United States and Canada.”
Get Certifications
The next step in this process is getting certified as an ethical hacker. You obtain this qualification by evaluating the security of computer systems, using penetration testing methods. There are many organizations offering training courses with certificates that you can earn to work as an ethical hacker.
These certifications are not always a requirement, but they can help your CV be more appealing to the hiring teams. In addition, it validates your knowledge and ability as an ethical hacker in networks, including troubleshooting, maintenance, installation and computer management.
So, this is the process to get started and grow in an ethical hacking career. Let’s move further in this Ethical Hacking Tutorial & Career Guide, ethical hacker certification salary and discuss some of the popular job roles that you can apply for in the field.
Ethical Hacking Job Profiles
Are you confused about the right career options available in Ethical Hacking? Below is the list of some of the most significant job profiles available in the industry. Take a moment to explore through the different job roles and find out which role might be ideal for you?
Hackers
A hacker is an individual seriously intrigued by the arcane and recondite activities of an operating system of the PC. Hackers are regular developers. Thus, hackers acquire propelled information on operating systems and programming dialects. They may find holes inside frameworks and the purposes behind such gaps. Hackers continually look for further information, uninhibitedly share what they have found, and never deliberately harm information. Hackers access the computer system or network without authorization. The negative side of hackers is they break the law which can lead to imprisonment.
Crackers
Crackers break into systems to steal or destroy data. A saltine is one who breaks into or generally violates the framework’s trustworthiness of remote machines with a vindictive plan. Having increased unauthorized access, crackers pulverizes essential information, deny authentic clients administration, or mess up their objectives. Crackers can without much of a stretch be recognized because of their malicious activities.
Ethical Hacker
Ethical hackers perform most of the same activities as hackers and crackers but the difference is that they hack the system with the permission of the owner. Ethical hackers by and large discover security exposures in shaky framework setups, known and obscure equipment or programming vulnerabilities just as operational shortcomings in procedure or technical countermeasures.
Script kiddies or packet monkeys
These are the young inexperienced hackers. They copy code and techniques from knowledgeable hackers. These techniques are learned by means of online hacking tutorials, various blog posts of famous hackers, or other online stuff.
Penetration Testers
Pen (or Penetration) testers write programs or scripts using various programming languages like practical extraction and report languages (Perl), C, C++, Python, Javascript, Visual Basic, SQL, and many other languages.
Now, you have some basic knowledge of the possible career options you have in ethical hacking. In the next section we will explore the best ethical hacker training courses available in the industry.
Certification Details: Why Taking an Ethical Hacking Course is Necessary?
These days, the demand for ethical Hackers is touching the sky due to the insufficient workforce, which makes the career opportunities and the salaries very attractive. Many professionals intend to enter and scale up in the industry. But just going through some ethical hacker tutorials is not enough. One of the recommended approaches, to begin with, includes Certification Courses.
The average ethical hacker salary in the USA is $120,000 per year. While it can go up to $156,780 per year for an experienced professional with ethical hacking certification.
Here are some of the best Ethical Hacking courses that are worth your investment and time.
Certified Ethical Hacking Training & Certification: This ethical hacker training course is designed to help you through the best hacking practices for writing codes. It helps you to learn protecting your company from security breaches, master in advanced network packet analysis and a lot more.
Cybersecurity Training & Certification: This course is more like a cybersecurity and hacking tutorial that helps you build a strong foundation in the domain. It is focused on different Cybersecurity essentials including Security basics, cryptography, network security, secure an app, data Security, user Security, Cyberattacks, user access & identity management, etc.
Getting certified with Ethical Hacker Beginner Course and Advanced Training is an ideal way to make the most of this increasing demand. We hope these hacking courses will help you with enhancing your skills and thus your profile.
A company may enlist an ethical hacker to endeavor to hack the computer framework inside specific limitations set by the organization and nation law. An organization may prepare their staff to play out this job in-house. Once in a while, ethical hackers are just self-broadcasted "nerds" who hack without anyone else's time, yet not dangerously. These sorts of programmers do it "for amusement only" and, in the event that they're abundance trackers, even get paid if they discover a proviso in an association's framework.
In the event that you choose to experience white-hat hacker training, you'll be in a phenomenal organization. For example, a little-known reality about Sir Timothy John Berners-Lee, most popular as the creator of the World Wide Web, is that he was a hacker in his initial years. As per Investopedia, "As a student at Oxford University, Berners-Lee was prohibited from utilizing the college PCs after he and a companion were discovered hacking to access limited regions."
One of the most famous white cap hackers in recent times is Kevin Mitnick, portrayed once by the US Department of Justice, as "the most wanted computer criminal in United States history." After spending time in jail for unlawful hacking, he improved and turned into a paid ethical hacking expert for various Fortune 500 organizations, just as for the FBI.
Final Words on Hacking Tutorial & Career Guide
Going through the different ethical hacker tutorials is a good start but the use of such techniques won’t make you a hacker, or an expert. It might make you a script kiddie. It usually takes years of study and experience to earn respect in the hacker’s community. It’s a hobby, a lifestyle, and an attitude. It’s a drive to figure out how things work.
Formal ethical hacking courses from a professional institution is perfect for hands-on training in a particular specialty. On the other hand, numerous hackers advocate self-learning, it is mainly suitable for those looking for guide on how to hack for beginners. The benefit of this is you get the opportunity to find your field specifically noteworthy. Overall, the Ethical Hacker role is an excellent career option if you are looking for growth and immense earning potential and want to stay relevant as per the market demand.
Hopefully, you found this ethical hacker tutorials guide blog helpful in understanding ethical hacking basics, how to become an ethical hacker, required certifications, skillset, career growth, salary range, and other aspects.
Happy Hacking but stay legal!
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
6 days 08 Jan 2026
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
0 day 02 Jan 2026
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
4 days 06 Jan 2026
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
7 days 09 Jan 2026
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
7 days 09 Jan 2026
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
0 day 02 Jan 2026
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
0 day 02 Jan 2026
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
0 day 02 Jan 2026
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 03 Jan 2026
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
15 days 17 Jan 2026
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
7 days 09 Jan 2026
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
8 days 10 Jan 2026
























Bradley Thompso
This is a perfect guide on How to become an Ethical Hacker. I was looking for such an amazing post from the last few days, but could not find one. Fortunately, I could go through this post and got so much information on the design. Thank you!
JanbaskTraining
Oh! That’s great. Thank you too for your valuable feedback.
Bryan Garcia
Wow..!! This Guide Towards making a career in Ethical Hacking is really helpful to understand its importance and what it includes. This is very helpful!
JanbaskTraining
That’s interesting to know. Let us know if you need any help.
Simon Martinez
The above Guide on the Ethical Hacking Career Path is just superb. Being a fresher in this field I have to keep myself updated with new tactics and tools. Thanks for sharing this post!
JanbaskTraining
This is quite motivating to hear that you found this post helpful and interesting.
Phoenix Robinson
Really good article with all the important information on ethical hacking. I got all my answers about this particular career path after reading this blog. Thanks for sharing this blog.
JanbaskTraining
That’s great! Let us know if you have any more questions.
Lane Clark
A comprehensive blog on an Ethical Hacker Career of this kind is what I wanted. This guide provides a lot of information without being lengthy or boring.
JanbaskTraining
Hopefully, you found it helpful. If you have any questions, feel free to write to us, we will be happy to help you.
Josue Rodriguez
Awesome blog! I have learned so much about how to become an ethical hacker, its significance, market demand, and a lot more. Thank you so much for sharing!
JanbaskTraining
It is great to hear that you found this post interesting. Often visit our website to read more!
Rafael Lewis
Such an interesting post! Very well explained, very understanding with so much information on Ethical Hacker Career Path.
JanbaskTraining
Sure, we will soon come up with a new guidepost on the Usability Of Icons In UI Design.
Colin Rodriguez
I found your blog today and it is very well written. Keep up the good work & share more about ethical hacking.
JanbaskTraining
That’s interesting to hear from you! Keep coming back to our website to read more content.
Rafael Lewis
Thanks for sharing this information on how beneficial it is to choose this career path. A lot of people want to know more about this and its benefits. so I’m really happy that I got to find your site before using it.
JanbaskTraining
It’s our pleasure that we could help you. Feel free to write to us if you have any questions.
Kyle Lee
Such an informative and great article! Every beginner in ethical hacking must read this article. This is very helpful for me and people who want to become an ethical hacker.
JanbaskTraining
Glad to hear that you found this post helpful! Often visit our site for more interesting content.