New Year Special : Get 30% OFF + $999 Study Material FREE - SCHEDULE CALL
New Year Special : Get 30% OFF + $999 Study Material FREE - SCHEDULE CALL
We live in an evolving digital world. The significance of cybersecurity law has never been more pronounced than today. There is a strong need for stringent cyber law now. You might be surprised, but the truth is that a hacker attack occurs every 39 seconds, and around 8,00,000 cyber attacks were recorded in 2023, as per the latest Security Magazine reports.
These alarming numbers of cyber attacks need discussion and implementation of strict rules. An increasing number of individuals and businesses rely on the Internet. This makes the cyberplace an essential aspect of our lives. We need to have some strict cyber laws to safeguard individual’s identity.
So, before jumping into the solutions, it’s vital to understand the “what is cyber law?” types of cyber crimes and how we can stay protected by recognizing the importance of cyber law plus the cyber security courses you can study to safeguard your virtual property and assets.
Now, let’s start this cyber law journey on this cyber platform.
Like other laws of the nation, state, or world, a cyber law exists in the digital realm to tackle the legal issues arising day by day. We have all heard about problems like data breaches, identity theft, malware attacks, and more. Around 33 billion accounts were breached in 2023, which converts to 2328 per day, accounting for 97 cybercrime victims per hour.
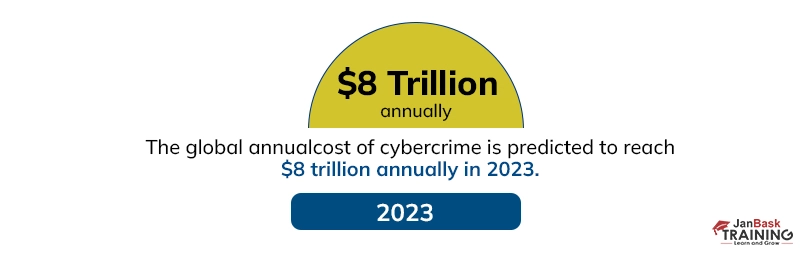
When we talk about cyber law, we describe internet law or information technology law as a specialized legal field that deals with legal issues arising in the digital realm. It encompasses various legal principles, regulations, and statutes that govern and regulate online activities, including the Internet, computer systems, networks, and digital data.
Cyber laws are essential in addressing the legal challenges and conflicts that arise in the rapidly evolving landscape of cyberspace. These digital laws seek to establish a framework for the responsible and lawful use of technology and the Internet while addressing privacy, intellectual property, digital security, and cybercrimes. It provides legal guidelines for individuals and organizations operating in the digital domain, ensuring their actions comply with the law.
Every law has a scope in the country, no matter for what purpose it is being framed. Similarly, after realizing the importance of cybercrimes or the alarming number of cyber crimes, IT experts have framed a few cyber laws to protect the intellectual property of individuals or businesses.
Below, we have explained the scope of cyber law in detail and helped you understand why you should seek online cyber security courses.
The importance of cyber law has been at the top of the list since the day online fraudsters and scammers came into place. This computer-generated comes under the gambit of some laws due to its worldwide jurisdiction system. Cyber laws are laws dealing with issues related to using inter-networked information technology. In other words, cyber law is the law governing computers and the internet.
Electronic commerce’s growth has propelled the need for vibrant and effective regulatory mechanisms to strengthen the legal infrastructure. It is so crucial to the success of electronic commerce. These governing mechanisms and legal structures come within the domain of cyber law.

The foremost reason behind cyber laws is to safeguard individuals' personal and confidential information on the web. Privacy threats have become more pronounced with the proliferation of internet connectivity and digital platforms. The strong set of cyber rules and regulations makes it important for organizations and individuals to handle their data with utmost confidentiality and availability.
Following the cyber laws becomes paramount to safeguard against unauthorized access, use, or disclosure of personal details. Anyone can confidently engage in digital transactions under the legal provisions of the cyber world to protect their sensitive data.
The importance of cyber laws is seen in data breaches and identity theft, where the legal frameworks devise remedies and redressal mechanisms for victims, giving the world a sense of security and trust in the digital ecosystem.
When someone asks about cyber law or its definition, we simply say the strict rules and regulations that prohibit unlawful activities. Protecting intellectual property is also very important, especially for all businesses. These laws address software piracy, copyright infringement, and digital content protection issues.
With these cyber laws, law enforcement agencies try incentivizing creativity, innovation, and technological advancements. Now, we can also see the importance of cyber laws with the newly created conducive environment for authors, businesses, artists, and inventors to protect their creations and inventions in the digital space.
Devising some legal solution against intellectual property violations, cyber laws create an atmosphere of respect for creative endeavors and encourage investment in research and development.
Cyber laws are vital in preventing and combating cybercrimes. They set rules and regulations that provide provisions and penalties for various digital offenses, such as hacking, identity theft, cyberbullying, online fraud, and harassment. Cyber laws criminalize these fraudulent activities and deter potential offenders from engaging in unlawful online crimes.
The benefits of cyber laws are evident, with a decent number of reduced crimes. Though the impact has not reached a greater extent, it has alerted people and penalized criminals.
Now, law enforcement agencies are effectively investigating and prosecuting offenders based on the legal frameworks provided. These cyber laws ensure that individuals and businesses can operate legally and safely in the cyber world. The simple motive behind framing these laws is fostering trust and promoting a vibrant digital economy.
Cyber laws provide a secure and supportive environment for e-commerce transactions. They form legal frameworks for electronic contracts, payment systems, and digital signatures. Cyber laws build trust among buyers and sellers, ensuring the enforceability of electronic transactions and the validity of digital signatures.
Law enforcement agencies provide legal recognition to electronic commerce and enable businesses to reap the benefits of the digital marketplace, expanding their brand’s reach and contributing to economic growth. The advantages are evident in the increased convenience and accessibility of secure online transactions, facilitating seamless trade globally.
Another benefit of cyber laws is that they provide individuals with effective redressal mechanisms for cyber offenses. Specialized cybercrime investigation cells and dedicated courts and tribunals are established to handle such cyber-related issues. These mechanisms provide timely resolution and justice for victims of cybercrimes, offering them a sense of security and trust in the legal system.
The importance of cyber laws worldwide is recognized with the efficient reporting and investigation process and prosecution of cybercrimes. It promotes accountability, hinders potential offenders, and reinforces the importance of responsible and ethical behavior in the digital realm.
Cyber law is sometimes also known as Internet law, and it is the law that deals with all the legal issues about the use of the Internet and digital communications. It is a broad field that includes digital acts, such as distribution, both software and hardware, access and usage of the Internet, and the security of this field. Most of the time, these terms are thrown in line with one another—the "cyber law," "what is cyber law," and "what are cyber laws,"—which determines that what concerns the public more is the ways through which those legal frameworks get adapted and modified under the advancements of technology.
The rapid evolution of cyber law in the last couple of decades, with the expansion of reliance on digital technology, has encompassed our professional and personal lives in the United States. Cyber law covers data protection, privacy, intellectual property rights, cybercrime, and e-commerce.
It lies at the base of cyber law. Several laws in the USA regulate the various issues of collection, storage, and sharing of personal information: the Children's Online Privacy Protection Act (COPPA) and the Health Insurance Portability and Accountability Act (HIPAA). The General Data Protection Regulation (GDPR) is a regulation of the European Union applicable to U.S. firms that process EU citizens' data, thus globalizing cyber law.
These rights are imperative in this digital era since content can be easily reproduced and distributed. Cyber law plays a crucial role in protecting the rights of the creator and innovator by enforcing laws about copyrights, trademarks, and patents. The Digital Millennium Copyright Act (DMCA) is at the core of online copyright protection as it has provided the legal framework for what may be described as the take-down mechanism of infringing works from sites.
With the development of e-commerce, the relation with consumers has also been changed. Cyber law takes care of consumer protection in the e-market, hence ensuring the enforceability of online contracts and the protection of consumers' rights. One such case is the Electronic Signatures in Global and National Commerce Act (E-Sign Act), 2000, which gives legal status to electronic contracts and makes them at par with any paper contracts in force in the country.
Therefore, cyber law in the USA is an ever-evolving area that attends to all the challenges and opportunities presented by the onset of the digital era. The legalities it covers are as wide as possible—from data protection and privacy to the rights attached to intellectual property and the crimes committed over the web—thus reflecting the complexity involved in the governance of the virtual world.
With today's technology, the time and scope of cyber law will surely expand a great deal. It will require and demand all involved, including professionals in law, business, and even ordinary individuals, to always be on their toes. One should be aware of cyber law and its consequences regarding the digital world and use the cyber world safely and responsibly.
Cyber Security Training & Certification

International cyber law is the special branch of law that addresses legal questions about using the Internet and digital technologies worldwide. It includes diverse legal systems and treaties that should apply to matters concerning the Internet, including digital communication, intellectual property, privacy, and cybersecurity.
Cyber law deals with the legal and regulatory dimensions of the internet and the digital environment about protection from and reaction to cybercrime, protection of the users' rights in the virtual environment, and, finally, aiming at setting data security.
One of the biggest challenges in international cyber law is the nature of the internet, as it does not recognize geographic boundaries. Such a widespread nature would require countries to unite to set legal standards and enforcement mechanisms in a coordinated manner. Key international agreements, such as the Budapest Convention on Cybercrime that promote such cooperation include elements of a need for common definitions of cybercrimes and provisions that promote mutual legal assistance between states.
Cybersecurity policy is necessary for an organization of any size to protect assets, data, and reputation from cybersecurity threats. The two strategies and policies fighting these cyber threats should be shifting, moving, and evolving in their assessment.
Thus, international cooperation and harmonization of cyber laws would be essential to creating a secure electronic environment where effective response and prosecution of cybercrimes across borders could occur.
Cyber law includes digital communication, intellectual property rights, data protection, and privacy, including electronic commerce (e-commerce). It responds to the challenges presented by cybercrime by offering legal systems that contain all these prevention, investigation, and prosecution processes. Below, we have included the names of the common cybercrimes. Let’s take a look.
Therefore, knowledge of cyber law is essential for every user on the internet since it defines what a person can do online and hence outlines realistic boundaries. It also demonstrates the importance of cyber security for defending against potential IT risks and providing legal protection to victims due to criminal offenses conducted by means related to information technologies.
Cyber law covers various matters like intellectual property rights, privacy, freedom of expression, internet access and usage. It is a keystone in the formation of a secure digital realm, the need therefore to those who wish to become a part of the cybersecurity industry.
The field of cybersecurity presents a diversity of positions, from the purely technical to governance and policymaking. Here are steps to advance in a cybersecurity career:It presents an image more appropriately.
The salaries in cybersecurity differ greatly in line with the level of experience, education, certification, and job role. Entry-level positions can pay from $50,000 per annum, with roles having experiences like CISOs earning more than $150,000 or even more a year. Specialization, higher certifications, and a comprehensive knowledge of cyber law can markedly hike the earnings.
Become an expert Cyber Security Professional with our EC Council Accreditation Course. Explore an extensive range of Cybersecurity essentials:

The crossroad between cybersecurity and cyber law is a field that is full of challenging opportunities. The bottom line of protecting yourself on the Internet is simple cybersecurity hygiene and respect towards the fundamentals of cyber law. The success of this dynamic field is navigated with a focus on a good educational foundation, relevant certifications, practical experience, and understanding of cyber law. The cyber security environment is ever-changing, and with the rising significance of digital security, technical and legal professionals are in high demand
Q1. What is cyber law, and why it is significant?
Ans. Content regulates the cyberspace covering the digital realm, including the internet, computers, and digital data. It is critical because it lays down rules for the use of technology for the right and lawful reason, it considers privacy, it protects intellectual property and it lays down regulations for cyber criminals.
Q2. Which are some of the most widely occurring cybercrimes that are defined by cyber law?
Ans. The usual kinds of cybercrimes include hacking, phishing, identity theft, cyberstalking, malware attacks, ransomware attacks, DDoS attacks, intellectual property theft, cyberespionage, and cyberterrorism.
Q3. What provides cyber law with protection to individuals and businesses?
Ans. Cyber law protects people and companies by ensuring confidentiality of personal information, IP rights and online business dealings. It creates legal environments around the protection of data, consumer rights, electronic contracts and cyber security measures, with legal remedies in cases of cyber crimes.
Q4. What are cyber laws advantageous?
Ans. The merits of cyber laws include privacy rights protection, sense of security in terms of intellectual property, avert cyber offenses, facilitate e-commerce transactions, enact redressal mechanisms of cyber offenses. These regulations foster trust, accountability and responsible conduct in the digital space.
Q5. What employment opportunities are there in cybersecurity and how does one become a practitioner?
Ans. Careers in cyber security are composed of jobs like security analysts, penetration testers, cyber security managers/consultants and CISO. Having a career in cybersecurity means education and training in computer science or similar fields, acquiring relevant certifications, having hands-on experience and staying abreast of cybersecurity trends and cyber law.
Q6. What salary expectations cybersecurity professional could have?
Ans. The salaries in cybersecurity tend to be different based on experience, education, certifications, and job positions. The latter can be either crucial or nonessential but are usually considered important. A beginner can start from an average of 50,000 dollars annually while highly experienced positions such as CISOs can earn over 150,000 dollars. Specialization, higher certifications, and knowledge of cyber law greatly influence remuneration.
Q7. How can one defend themselves on the internet?
Ans. People can self-protect themselves on the internet through cybersecurity hygiene including use of strong passwords, software update, suspicious email/link avoidance, and use of reputable security software. Furthermore, cyber law comprehension allows people see their rights and online legal protections.
Q8. How is cyber law related to cybersecurity?
Ans. Cybersecurity and cyber law are two interrelated areas which jointly provide a secure and lawful digital environment. Cybersecurity is concerned with securing digital assets and systems against cyber threats whereas cyber law establishes legal regulations to regulate online activities, punish cybercrimes, and protect individuals' rights and privacy. Grasp of both of them is essential for preserving security and compliance in the digital era.
The JanBask Training Team includes certified professionals and expert writers dedicated to helping learners navigate their career journeys in QA, Cybersecurity, Salesforce, and more. Each article is carefully researched and reviewed to ensure quality and relevance.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Interviews