Introduction
If you aspire to become a cybersecurity professional and work for top companies, this time is the perfect opportunity for you. The cyber awareness need of 2024 starts with the need to understand “What is Cybercrime” and “What are the Different Types of Cybercrime?” followed by a detailed understanding of the concept either through cyber security classes or other credible online resources that can not only help you as a professional to excel but also help the netizens protect themselves from the choppy threats over the internet. So, a cybersecurity course is valuable for all.
The advent of technology has indeed enhanced human capabilities to meet the challenging needs of the competitive environment today. Still, the vulnerabilities in the technological architecture, including the computer networks and devices, have laid the foundations for online cheating, fraud, and theft. As such, cyber awareness is the only effective tool that can neutralize online threats and attempts.
In this article, we will focus on understanding the core concepts of cybercrime by taking on elaborate questions like what cybercrime is, what the different types of cybercrime are, and what the right approach to cybercrime prevention could be.
We would also recommend going through JanBask’s cybersecurity certification programs designed to equip our students with knowledge and resources to fetch the most demanding jobs in the cybersecurity landscape.
What Is Cybercrime and Who Creates Cyberthreats?
So, what is cybercrime? Crimes performed over the internet using digital devices and technologies are called Cybercrime. The intent behind performing a cybercrime could range from professional to personal benefits. While things mostly revolve around financial benefits, technological misuse to commit personal reputational damage and spread vulgarity is equally prevalent.
People who commit illegal and criminal activities over the internet are cybercriminals. It can be an individual or an organization hiring spammers to meet a paid objective, possibly for a company or political organization. It has also been noticed that employees working in cybercrime organizations start individual operations, gaining experience and expertise over time. This indicates that the risk of cybercrime exposure is increasing with time, and the need to undertake some basic cybersecurity classes to preserve cyber safety is mandatory to understand all the scenarios of threats over the internet.
The History of Cybercrime
After learning about what is cybercrime, let’s offer you some facts on the history of cybercrime. The history of cybercrime began in the 1970s with early computer hacking and data theft. As technology evolved, so did criminal tactics, leading to increasingly sophisticated attacks such as viruses and phishing attacks in the 1990s. Today, cybercrime encompasses a wide range of activities, from ransomware to identity theft, affecting millions globally.
What are the Types of Cybercrime?
We have listed some prominent types of cybersecurity threats that are common on the internet these days. However, please be informed that this list is not exhaustive. Cybercriminals are continuously developing tools and methodologies to counter software updates and carry out cyber attacks. Let us now move on to understanding the types of cybercrime, as mentioned earlier, with examples.

Types of Cybercrime with Example
Internet threats and crimes can be classified into categories of cybercrime. The four main categories of cybercrime are
- Cybercrime types that target Individuals.
- Cybercrimes that target business houses.
- Activities that threaten national security can take many forms, including various types of cybercrimes also known as digital crimes. Despite being classified, these cybersecurity threats can often be combined to achieve malicious objectives. Understanding each type of cybercrime individually provides a comprehensive view of the tactics used online. If you are interested in pursuing a career in cybersecurity or simply want to learn more about different types of cybercrimes and their prevention, we can start with reading cybersecurity books followed by a cybersecurity course from a credible institution.
- Criminal Activities that pose a threat to society.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
1. Email Scams (Phishing attacks)
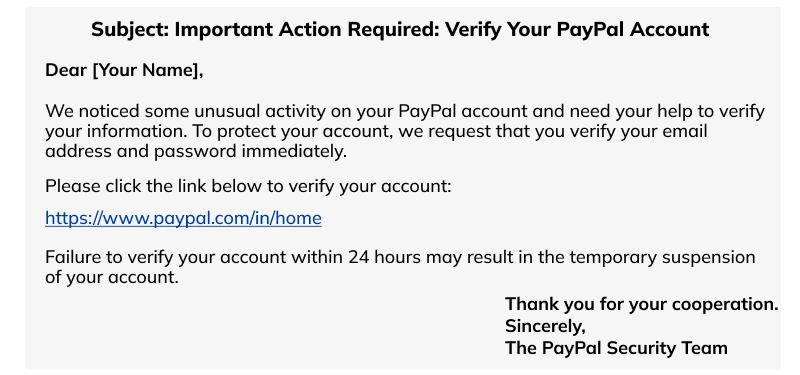
Email scams or phishing and pharming are the most common scams that make deceptive attempts to collect personal information like usernames, passwords, and bank details. The operational method involves sending fake emails with links to redirect users to a bogus website that looks and claims to be the original entity.
Example of Phishing attacks Scam:
This type of Cybercrime involves sending scammy emails to users, dupped as an original business house with which the user holds an account. The email domain looks similar to a genuine company but is forged. Here’s a sample email:

2. Financial Scams
Financial scams can be multifaceted. Scammers draft fake schemes promising huge returns on investments or fake online marketplaces that offer cheap products (digital and physical). The attackers either ask for investment-sensitive bank account information or payment card information.
Example of Financial Scams:

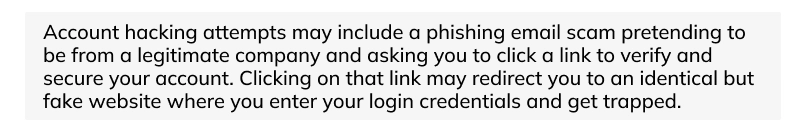
3. Account Hacking
Under Account Hacking Cybercrime among the 50+ types of cyber attacks cybercriminals get unauthorized access to an individual’s or an organization’s account to make changes in the account to hamper the reputation of the person or the organization or steal some data to make monetary gains.
Cybercriminals use several methods and tools to hack accounts, including password guessing, phishing emails, asking to click on links, etc.
Example of Account Hacking Cybercrime:

4. Malware Attacks (Virus Attacks)
In this type of cyberattack,, attackers target your computer system, infecting it with malicious software or a virus sent to you as a link in an email.
Example of Virus Attack on Computers:

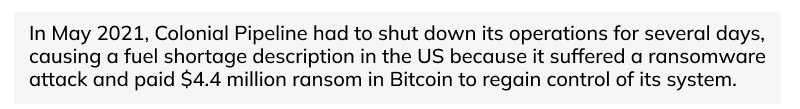
5. Ransomware Attacks
Ransomware attacks encrypt a user's files or entire systems. Cyber attackers then demand payment to release the systems.
Example of Ransomware Attacks:

6. Data Theft or Data Breach
The modus operandi in data theft type of cybersecurity threats is exploiting vulnerabilities or using hacking techniques to access the databases to steal sensitive information, including personal, professional, corporate, and financial data. The data compromised may include critical personal or business details like trade secrets, training details, financial details or records, etc.
Example of Data theft cybercrime:

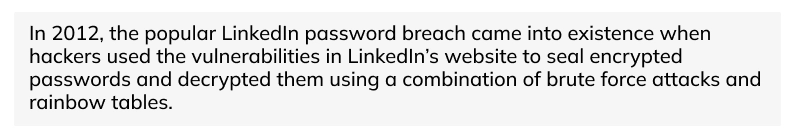
7. Password Breach
Password breaches are cases when cybercriminals in your database, maybe your social, professional, or financial account, breach your passwords. Hackers employ various techniques, including basic-level techniques like guessing a password, as well as advanced tools to exploit vulnerabilities in a website to breach the passwords. Some popular techniques used by hackers are as follows:
- Keylogging: Attackers install malicious software (keyloggers) on a victim's device to record keystrokes, capturing passwords and other sensitive information as it is typed.
- Social Engineering: Attackers manipulate individuals into revealing their passwords or other sensitive information through deception or psychological manipulation. This can involve impersonating trusted figures or creating scenarios that pressure the victim into providing access.
- Man-in-the-Middle Attacks: Attackers intercept and potentially alter communications between the victim and a legitimate service to capture passwords and other data. This is often done on unsecured or compromised networks.
- Password Cracking Tools: Attackers use specialized software to crack encrypted passwords by exploiting weaknesses in encryption algorithms or by using precomputed tables of hash values (rainbow tables).
Also read, Is It Safe To Store Passwords in Chrome?
Example of Password Breach Cybercrime:

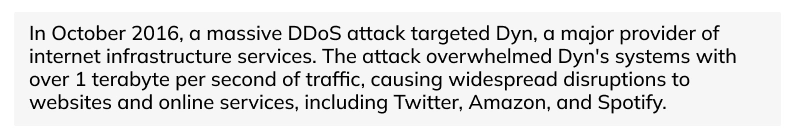
8. Distributed DoS attacks
Distributed DoS attacks (DDoS) are one of the types of digital crimes that cybercriminals use to bring down a system or network. A DDoS attack infects systems using standard communication protocols to spam the system with connection requests. Cybercriminals who carry cyberextortion may use the threat of a DDoS attack to demand money.
Example of DDos attacks:

9. Identity Fraud
Identity fraud cybercrimes occur when cybercriminals use stolen personal information to impersonate individuals for financial gain. Victims may face financial losses, damaged credit, and legal consequences unknowingly due to this type of cybercrime.
Example of Identity Fraud Cybercrime:

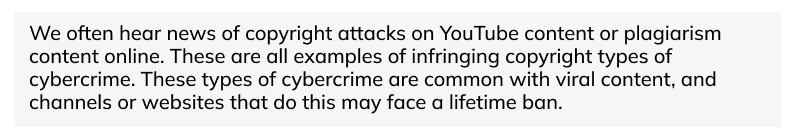
10. Infringing Copyright
We often encounter fake or duplicate copies of publications or other forms of content online and offline. These are the unauthorized use of copyright materials, and creating or distributing these materials is a type of cybercrime known as Infringing copyright.
Example of Infringing Copyright:

11. Cyber Espionage
Cyberespionage is yet another way to steal sensitive information and data from a network of computers. The modus operandi is to access data silently for a longer time, and thus, these types of cybercrime are widely designed to steal information for political, economic, or military purposes, which are against cybercrime laws.
Example of Cyber Espionage Attacks:

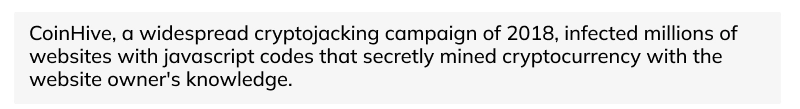
12. Cryptojacking
In cryptojacking, hackers gain access to websites through various types of cybercrime and infect them with codes that secretly mine cryptocurrencies for the hackers, which are against the cybercrime laws.
Example of Cryptojacking Attacks:

13. Cyber-Extortion
Cyberextortion is a type of cybercrime that involves threatening an individual or an organization to damage its system if not paid a ransom. This can be a pre-cyber attack threat or one given after gaining access to a website.
Example of Cyber Extortion Cybercrime:

14. Illegal Items Selling
Selling illegal or unapproved items online is on the rise and is a serious threat to society. The Dark Web Marketplace is probably the most common site where illegal trades occur. This type of cybercrime involves selling drugs, weapons, and other commodities that are harmful to society and are banned legally.
Example of illegal Items Selling Websites:

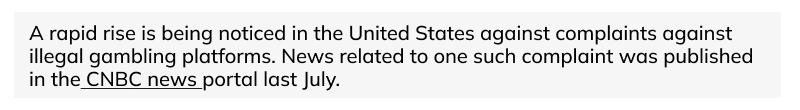
15. Restricted Gambling
Countries have laws to govern online gambling activities, and involvement in restricted gambling by exploiting legal loopholes or using an illegal platform is a type of cybercrime. Users must adhere to local regulations and choose licensed gambling platforms to avoid legal repercussions.
Example of an illegal Gambling Website:

The Impact of Cybercrime
The impact of cybercrime is huge and widespread. It crosses boundaries to damage individuals and organizations with financial losses, reputational damage, security threats, and operational disruption. We have seen in the examples above how the different types of digital crimes compelled even giant organizations to halt their operations for weeks and pay ransom.
There have been several studies by reputed organizations, including federal reports, to analyze the impact of cybercrime, and the following are some data obtained that illustrates how the different types of Cybercrime are creating losses to organizations and individuals.
This includes:
- According to the IBM Cost of Data Breach Report, the average data breach cost in 2022 was $4.35 million.
- The U.S. Treasury Department's Financial Crimes Enforcement Network (FinCEN) states that ransomware payments reached $41.4 billion in 2022.
- A 2022 report by Cisco found that 60% of organizations have experienced a business-disrupting ransomware attack in the past year.
- A 2022 report by IBM found that 52% of consumers would not do business with a company that has experienced a data breach.
- The U.S. Cyber and Infrastructure Security Agency (CISA) report for 2023 found that there were 614 significant cyber incidents.
Why are Cybercrimes Increasing?

There are various reasons why cybercrimes are increasing, and one primary reason is the difficulty of investigating and prosecuting. While internet accessibility is unrestricted over different regions, legal jurisdiction does not allow cross-investigation over boundaries. Creating a false identity is easy on internet networks, and disbanding accounts makes it hard to trace the root of digital crimes, especially across international borders. This is why big industries are in dire need of talented cybersecurity engineers.
The Other reasons behind growing cybercrimes include but are not limited to:
1. Vulnerable Devices:
A major reason behind the rising number of cybercrime instances is the presence of vulnerable devices and technologies. The Internet allows connecting with other devices and accessible files on a system; as such, scammers have developed tools that evade security and make stealing critical information over the network easy.
2. Technological advancements:
While on the one hand, technological advancements are creating new opportunities to develop highly efficient tools that make information sharing and accessibility easy, on the other hand, cybercriminals are using the advent of technology to develop tools and software that cause obstruction and damage the operation of an application or a computer. Instances arise when software denies service to a subscriber (D’os attack) and data associated with the software is compromised.
3. Lack of Cybersecurity Awareness:
Lack of security awareness is common among people and organizations. While non-techy folks favor free digital stuff, many organizations have weak cybersecurity infrastructure to safeguard the organizational interest against cyber attacks. In both cases, systems are exposed to hackers for committing various types of Cybercrime.
4. Increased Reliance on Technology:
The Increased reliance on technology has connected our various devices for technology access. With each device needing security measures, any vulnerability may extend the attack surface for cybercriminals. Further, our increasing subscriptions and digital accounts distribute our data over the internet. Any weak platform lacking adequate cybersecurity infrastructure may lead to a data breach.
Cyber Crime Prevention & Critical Tools
Finding a single solution to counter the rising cybercrime threats is practically impossible. Individuals and organizations need to develop tools, follow best operation practices, obey the guidelines, and boost awareness to counter cyberattacks effectively.
Some preventive measures may include but are not limited to the following:
- Implementing strong cybersecurity measures: Installing genuine firewalls and intrusion detection systems.
- Educating employees about cybersecurity: Training employees to identify and report suspicious activity is crucial to prevent cyberattacks.
- Keeping software up to date: Regularly updating operating systems, applications, and firmware.
- Using strong passwords and multi-factor authentication
- Backing up data regularly
- Proactive Responses
- Removing the malicious software or code
- Notifying affected parties
- Analyzing the incident and planning measures to prevent any future cyber-attack.
Suppose you’re reading this blog to develop an in-depth understanding of cybercrime and cyber security and are willing to make a career as a cyber security expert. In that case, our next section will help you take the initial steps!
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
Skills Required To Become a Cyber Security Expert

Cybersecurity experts play a crucial role in mitigating the various types of Cybercrime. Besides providing personal protection, the essential cybersecurity skills that lead to cybersecurity expertise can fetch you an attractive career in the IT sector. Now, what are those essential skills? Let’s take a walk through the essential skills that are required to become a Cybersecurity Expert.
As we all know, cybersecurity is a vast field with a constantly evolving landscape. Here's a breakdown of essential skills to consider:
Technical Skills
- Networking and System Administration: Understanding network infrastructure, protocols, and system administration is fundamental.
- Operating Systems: Proficiency in various operating systems (Windows, Linux, macOS) is crucial for identifying vulnerabilities and implementing security measures.
- Network Security Control: Knowledge of firewalls, intrusion detection/prevention systems, VPNs, and other network security tools is essential.
- Malware Prevention and Detection: It is crucial to understand malware types and their behavior and to use antivirus and anti-malware software.
- Coding and Encryption: Proficiency in programming languages and encryption techniques is beneficial for developing security solutions.
- Cloud Security: With the increasing reliance on cloud platforms, understanding cloud security architectures and best practices is vital.
- Blockchain Security: Knowledge of blockchain technology and its security implications is becoming increasingly important.
- IoT Security: As the number of IoT devices grows, securing these devices becomes a critical area of expertise.
- Artificial Intelligence (AI): AI can be used for both offensive and defensive purposes in cybersecurity. Understanding AI and machine learning is valuable.
Soft Skills
- Problem-Solving and Analytical Thinking: Cybersecurity professionals need to be able to identify, analyze, and resolve complex security issues.
- Communication Skills: Effective communication is essential for explaining technical issues to non-technical stakeholders and collaborating with team members.
- Attention to Detail: Cybersecurity often involves meticulous analysis of data and systems to identify potential threats.
- Adaptability: The cybersecurity landscape is constantly changing, so professionals must be able to adapt to new technologies and threats.
- Teamwork: Collaboration with other IT professionals is crucial for effective security management.
Additional Skills
- Incident Response: The ability to respond to security incidents efficiently and effectively is a valuable skill.
- Digital Forensics: Investigating cybercrimes and recovering digital evidence requires specialized skills.
- Risk Assessment and Management: Identifying, assessing, and mitigating security risks is essential for protecting organizations.
- Compliance: Understanding and adhering to relevant cybersecurity regulations and standards is crucial.
- Remember: The specific skills required will vary depending on the cybersecurity role you pursue. Continuous learning with relevant certifications is essential to stay updated with the latest threats and technologies. Let’s learn about some crucial cybersecurity certifications.
Cyber Security Certifications
Get ahead of the curve with trending cyber security courses available online and earn globally recognized top cyber security certifications that will uplift your career. The online cyber security courses enable you to gain basic to advanced cyber security skills and techniques to defend against cyber threats. Enroll now for CyberSecurity Training and learn how to be a cybersecurity engineer.
Eligibility For Cybersecurity Online Courses
Candidates should have a bachelor’s or equivalent degree. Candidates with a basic understanding of Database Applications and Network Security should apply for career advancement opportunities.
|
Courses
|
Certification
|
|
Cyber Security - Master
|
EC Council Accreditation - Cyber Security Training & Certification
|
|
CISSP
|
New Age Online CISSP Training & Certification
|
| CEH- Master |
Certified Ethical Hacking Training & Certification
|
How JanBask Training Can Help!
Everything good has a flip side, and so will technological developments. To counter these flipping effects, we will need awareness that helps us take measures to prevent the ill effects. Cybercrime is a similarly evolving threat widely affecting individuals' lives and organizations' operations. The awareness needed in this space goes beyond the need to understand what cybercrime is or the types of Cybercrime. Educating ourselves and others about cybercrime is crucial to detecting, responding, and preventing threat incidents and promoting a culture of cybersecurity.
We must also adhere strictly to safe practices that prevent adopting strong cybersecurity practices, such as using strong passwords, keeping software up to date, and being cautious about what we click online, and following cybercrime laws.
At JanBask, we have specifically designed cyber security courses and certification programs that range from weeks to months and include cyber security certificate programs as well as cyber security degree online programs, imparting you with a need-based exposure to meet the internet threat challenges. Let’s join hands together. Working together can make our digital world safer and reduce the impact of cybercrime.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
FAQs
Q1. What are the types of cybercrime?
Ans- Types of Cybercrime are:
- Phishing attacks
- DDoS attacks
- Identity theft
- Ransomware
- Cyberstalking
- Internet fraud
- Cyber crime
- Cyber espionage
- Data breach
Q2. Explain types of Cybercrime with examples.
Ans- There are diversified types of cybercrime recorded across the globe, and some of the noteworthy examples are email fraud, social media fraud, banking fraud, ransomware attacks, cyber espionage, identity theft, clickjacking, and spyware. Let's explore how these crimes are carried out.
Q3. How Cyber-crime prevention can be done?
Ans- Five easy tips for cyber crime prevention-:
- Check if you've already been involved in a data breach. Visit haveibeenpwned.com and change those passwords for any accounts that it suggests may have been compromised.
- Check the strength of your passwords.
- Avoid these passwords.
- Trust no one (on emails)
- Secure your device.
Q4. Are cybersecurity certification programs good for your career?
Ans- The cybersecurity certification program is important because it provides tangible evidence of a person's knowledge, skills, and expertise in the field of cybersecurity. It helps individuals stand out from other candidates in the job market and can also help them advance their careers within their current organizations. Earn a cyber security certificate by enrolling in Cyber Security classes.
Q5. Where can I get a cyber security degree online?
Ans- Get Ahead Of The Curve With Janbask's Cyber Security Courses Online.
Our online cyber security courses enable you to gain basic to advanced cyber security skills and techniques to defend against cyber threats. Enroll now for cybersecurity certification programs and Get Expertise in securing your Critical Systems with the cyber security certificate.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
2 days 10 Jan 2026
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
2 days 10 Jan 2026
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
7 days 15 Jan 2026
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
1 day 09 Jan 2026
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 09 Jan 2026
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 16 Jan 2026
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
2 days 10 Jan 2026
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
2 days 10 Jan 2026
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 09 Jan 2026
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
9 days 17 Jan 2026
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
1 day 09 Jan 2026
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
2 days 10 Jan 2026