Year End Sale : Get Upto 50% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL
Are you interested in knowing about the concept of cybersecurity, what is it, and why is it important? What are the top cybersecurity certifications for beginners to help you grab potential opportunities? Is it mandatory to have an IT degree to walk the cybersecurity career path successfully, or can it be done just after completing a cybersecurity training course?
This post will discuss all you need to know about a cybersecurity career, along with a brief introduction to cybersecurity.
Are you ready to take a cybersecurity ride?
Let’s start with an intriguing statistic.
According to the World Economic Forum, The worldwide talent deficit, affecting various countries and industries, could lead to a shortfall of 85 million workers by 2030, resulting in an estimated $8.5 trillion in lost annual revenue. Specifically, the global cybersecurity sector urgently requires four million professionals to address its talent shortage.
This data highlights that there is no dearth of opportunities in this domain. You just need to start your career trajectory the right way.
We live in the digital age where data is everything & we need to understand more about cyber security and what is it. From growing data breaches and cases of identity theft to loss of critical personal & business information, it's crucial for mass to understand why is cybersecurity so important & realize that it's far more vulnerable than ever before.
CISA says since 2021, there has been a ransomware attack every 11 seconds in the US alone, with 43% of small businesses being its first target.
As data breaches, hacking, and cyberattacks reach new heights, Small or big, every business and institution is struggling to protect their data from hackers and cybercriminals, increasingly relying on cyber security experts to identify potential threats and deal with them to protect valuable data. But, you can play a vital role here by understanding what is cybersecurity, learning about cyber security and its opportunities, mastering the skills effectively & developing a fruitful career in it by skillfully reducing the lifecycle and impact of breaches when they occur!
So, if you are a beginner, & wondering about cyber security what is it, stay tuned, as we are going to unfold each section in detail, beginning with the concept itself!
Down the post, you will essentially learn about-
And much more…
Let’s start by exploring what is cybersecurity?
Cybersecurity is the art of protecting networks, devices, and data against unauthorized, unethical access for criminal or fraudulent use and the practice of guaranteeing network & data confidentiality. A subset of IT security, cybersecurity focuses primarily on protecting digital assets from vectors of digital attacks.
With so many access points, public IPs and constant traffic, and tons of data to exploit, hackers are exploiting vulnerabilities and creating malicious software for the same.
However, cybersecurity is based on detecting, mitigating, and remediating cyber attacks with advanced technology solutions. Unfortunately, the industry’s lack of skilled cybersecurity professionals is one of the primary reasons businesses cannot sustain increasing cyberattacks. Hence, cybersecurity aspirants can leverage this gap to become highly sought-after cybersecurity professionals industries are searching for.
International Data Corporation (IDC) says AI in the cybersecurity market is growing at a CAGR of 23.6% and will reach a market value of $46.3 billion in 2027
So, this was a concise cyber security introduction that helped you understand. In the next section, we are going to help you understand how cybersecurity is important for businesses.
Cyber Security Training & Certification

After the introduction of cyber security, you should also learn about its importance in business to know the roles and responsibilities of cybersecurity professionals better.
Cybercriminals attempt to access, change, or destroy data, extort money from users or the organization, or aim to disrupt typical business environments & operations.
Cybersecurity measures are designed to combat security threats against networked systems and applications. IBM says the global average cost of a data breach in 2023 was USD 4.45 million, a 15% increase over 3 years in the United States. These costs include economic costs (cost of repairing damaged systems, cost of downtime, and lost revenue), regulatory costs (including regulatory fines or sanctions costs), and reputational costs (loss of consumer trust and loss of customer loyalty).
Cyber attackers target customers’ personally identifiable information (PII)—including names, addresses, national identification numbers, and credit card details—and then sell these records on the dark web and underground digital marketplaces. Compromised PII often leads to a significant loss of brand reputation and loyal customer trust, along with the imposition of regulatory fines and legal action.
Organizations with a comprehensive cybersecurity strategy, guided by best practices and enhanced with advanced analytics, artificial intelligence (AI), and machine learning, can effectively combat malicious cyber threats. This approach helps create a secure web environment and protects their hard-earned brand reputation.
Well, hope you get a clear picture of cybersecurity and why we need it!
Having said that, let’s now move on to the next section and explore critical cybersecurity subdomains & CIA Triad to understand cybersecurity and its importance!
The core importance of cybersecurity in business is that a robust cybersecurity strategy has layers of multi-domain protection to defend and fight back against cyber-attacks and protect organization data, network, and architecture from fraudulent activities.
To best answer the question “What is cyber security” and how cyber security works, we must divide it into a series of subdomains:
Here are the critical cybersecurity domains cybersecurity experts consider to identify potential threats and protect valuable data.
All the critical subdomains are an integral part of the end-to-end Cybersecurity Model to defend the network from cyberattacks that are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting or hampering business operations & processes.
Next, we help you explore what cybersecurity CIA Triad is and how it plays a foundational role in security systems development to keep your data safe and secure against growing cyber threats.
The CIA triad refers to an information security model comprising three principles: confidentiality, integrity, and availability. Each of these components represents a fundamental objective of information security, vital for enhancing data security posture, and helps organizations stay compliant with complex regulations, and ensures business & operation continuity.
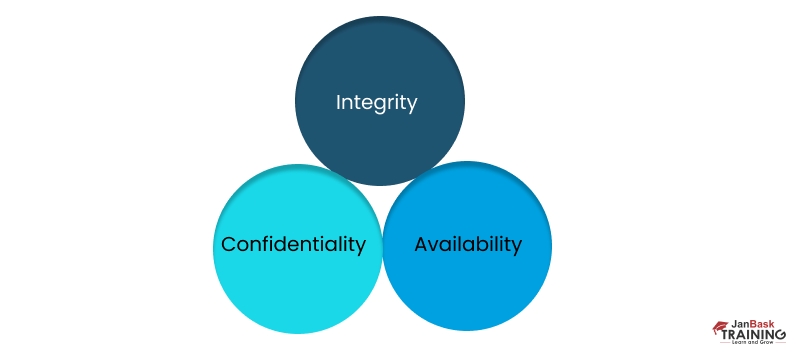
Priority of these principles may suffer, depending on an organization’s security goals, industry, regulatory requirements, or nature of your business.
For a better understanding of what is cybersecurity and the importance of cybersecurity in business, let's explore some of the most common but critical cybersecurity threats, which are malicious attacks seeking that seek to unlawfully access data, disrupt digital operations, or damage critical information.
Getting hacked isn’t the only threat to data confidentiality; it can also ruin their relationships with customers. The need to protect confidential information is a pressing concern at the highest levels of government and industries across the globe. There are dozens of types of cyber security threats. Let’s explore some critical ones.
Exploring all these threats helps you understand why cybersecurity is so important to provide security solutions to help organizations drive security into the fabric of their business so they can thrive in the face of uncertainty.
Depending on the nature of the business, some industries are more vulnerable to cyber threats than others. An organization that holds sensitive data or personally identifiable information is a common target for hackers. Types of institutions or organizations that are most vulnerable to cyber attacks include
The frequency of malicious breaches is growing at a massive pace. The volume of sensitive personal and financial information stolen is higher than ever before and the industry is confronting a heavy shortage of cybersecurity professionals.
“Cyber Security services, which include planning of cyber security strategies, policy development, and building security architecture, are expected to grow at a compound annual growth rate (CAGR) of 9.7% over 5 years to become a market worth over $345 billion by 2026.”
These stats are more than enough to show you the growing demand for skilled cybersecurity professionals in the coming years.
In the introduction to cyber security paragraph, we've already mentioned how huge the demand for talented cybersecurity professionals is in the job market. Now, if you wish to learn about cybersecurity and build a growthful career in cybersecurity, let’s move ahead and explore cybersecurity career trends and growth scope.
To get started with cybersecurity, take some time to develop core IT skills, including programming languages, networking skills, systems administration, and cloud computing. While you don’t necessarily need a degree to get a job in cybersecurity, having the accredited and structured cybersecurity training and the right certification combined with solid industry experience to get the right level of skillset might accelerate your path toward your dream job.
Before you apply for your first cybersecurity role, you must know these Cyber Security Prerequisites:
Cyber Security Training & Certification

Many employers often demand certifications as a prerequisite for employment, having Cybersecurity certifications validate an individual's level of knowledge & expertise. Let’s see the most demanding cybersecurity certification for beginners & experienced levels.
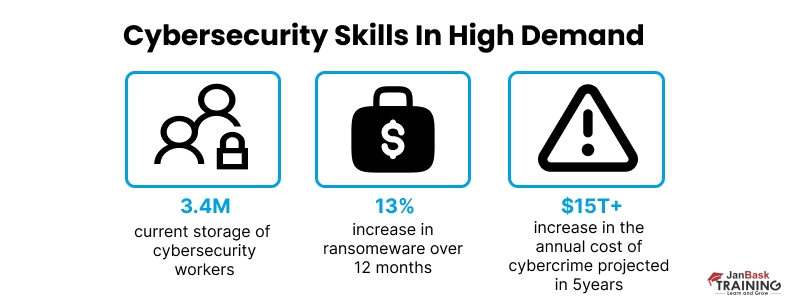
The most in-demand cybersecurity certifications:
Cyber Security Training & Certification

Accredited cybersecurity courses and enquiring about any of these cybersecurity certifications can help you earn good salaries. Here are some more benefits of acquiring a cybersecurity Certification.
Next, we are going to explore the most demanding cybersecurity job roles with their median salaries.
Suppose you’re new to cybersecurity and want to have a career. In that case, you can start in an entry-level IT role, such as a help desk technician, network administrator, or security software developer. You can enter this field as a junior information security analyst after gaining some experience in IT. Individuals who seriously want to grow their careers in cybersecurity can explore this cybersecurity salary guide for a much-needed motivational boost.
As already mentioned, organizations are in dire need of cybersecurity professionals with the right amount of awareness and hardware and software skills. Let’s explore some of the security roles with a raving demand:
The top 5 paying industries for a Cyber Security Engineer in the United States, estimated by Glassdoor:
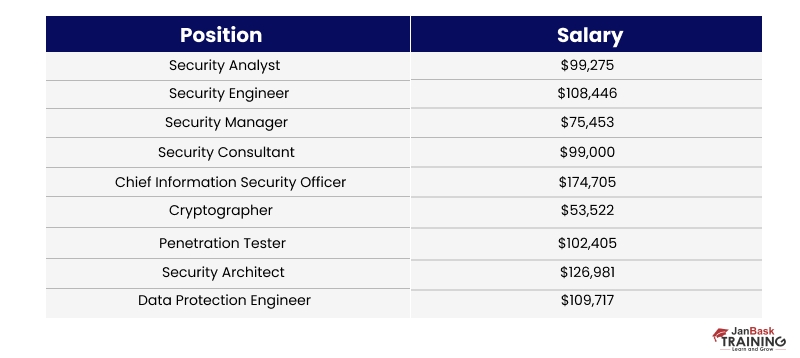
Security is not just about mastering technology; it is about contextually applying it. The key is knowing the environment and applying appropriate controls. Enterprises look for professionals who have knowledge of both. As the industry confronts a severe shortage of cybersecurity professionals, it often becomes challenging to get the right talent, which is why organizations are willing to pay them heavy checks. Go through each role in detail and research on the net, and learn about the Best Cybersecurity Certifications for the Year 2025. You can also refer to this blog on how to become a cybersecurity expert for some help and start your rewarding journey in this domain.
In this evolving and ever-dynamic cyber threat environment, organizations need a highly agile skillset and up-to-date cyber professionals to ensure a secure web environment and help organizations stay ahead of the curve. With many technologies and evolving domains, especially cloud and data security, finding the right talent is a huge challenge. Since there is a large demand versus supply gap in the talent market, growing your career in cyber security with the accredited cybersecurity training course with the most suitable and demanding cybersecurity certification for beginners ensures a growthful, successful career.
If you wish to learn cybersecurity skills and build a secure and prolific cybersecurity career, check out our Cyber Security Certification Training, which comes with instructor-led live training and real-life project experience. This cybersecurity training course will help you understand cybersecurity in-depth and help you achieve mastery over the subject.
Did we help you understand what is cybersecurity and why it is essential? Or do you still have some doubts or maybe you want to add something to your knowledge? Let us know in the comments below!!
Q1. What is cyber security?
Ans- Cyber security is defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. Cybersecurity safeguards systems, networks, and programs from digital attacks. These cyberattacks are done to know, change, or destroy sensitive and valuable information, blackmail money from users via ransomware, or create hindrances in everyday business processes.
Shape up your career with cissp training online and earn cyber security training and certification.
Q2. What does cyber security do?
Ans- if you are wondering what does cybersecurity do, here is your answer. Cyber security safeguards computers, data, networks, systems, and information from cyber thefts. This field has multiple specializations, each focusing on a distinct area of digital defense, such as protecting networks, information security, and recovery from any disaster.
If you want to specialize in an area, get a cissp certification online.
Q3. What is the scope of cyber security?
Ans- Cyber Security initiatives including backup, cryptographic controls, vulnerability management, incident management, technical compliance checking, security testing and auditing, collection, maintenance, and protection of evidence, including logs and audit trails, authentication, and access of sensitive information.
If you want to build a career in this field, look up cissp training online and get cyber security training and certification to gain knowledge on cyber security definitions, cyber security examples, cyber security information, and cybersecurity meaning.
Q4. Which certification is required for a cyber security job?
Ans- Here are some certifications that one would require to secure a job in the field of cybersecurity. Join cybersecurity certification classes and learn what is cyber security, what does cyber security do, and cyber security definitions.
Q5. How much salary can we expect in cyber security jobs?
Ans- Careers in cyber security are touching the sky. With growing digital needs, there are increasing threats to the data and other essential information, resulting in increasing job opportunities in this field and more pay than expected. Get a cissp certification online.
According to GlassDoor, the estimated total pay for a Cyber Security is $102,193 per year in the United States, with an average salary of $95,304 annually.
Q6. What qualifications do you need for cyber security?
Ans- A computer science, information systems, or programming BA would suit positions like security specialists, analysts, and web developers. However, some positions require relevant practical experience with a degree. Get cyber security training and certification by joining a cissp training online. Get to study cybersecurity meaning with relevant cyber security examples.
Q7. How long does it take to become a cybersecurity specialist?
Ans- One can acquire an entry-level position within the initial years of their career journey, such as a cyber security engineer. And if someone has experience in the IT industry with proper training and a cissp certification online, their career will take off quickly.
Q8. What are the benefits of cyber security jobs?
Ans- These are the top 3 benefits of cyber security.
Every organization has a high cyber security panel for a safe and secure environment. You, too, can grasp the opportunity by getting into cyber security. Join cybersecurity certification classes and gain in-depth knowledge on what is cyber security, what does cyber security do, cyber security definitions, and cyber security examples.
Q9. What is the importance of cyber security?
Ans- Cybersecurity is essential in every field because it secures all categories of data from theft and damage. This includes sensitive data, personally identifiable information (PII), protected health information (PHI), personal information, intellectual property, data, and governmental and industry information systems.
If you want to be a part of this important industry, you should know what does cybersecurity do and cybersecurity meaning. Get cyber security training and certification online.
Q10. What are the benefits of a cyber security course?
Ans- here are some Top benefits of cybersecurity training:
You, too, can enroll in cissp training online and skyrocket your career in this field. Learn all about what does cyber security do, cyber security definitions, and cyber security examples with some cyber security information.
The JanBask Training Team includes certified professionals and expert writers dedicated to helping learners navigate their career journeys in QA, Cybersecurity, Salesforce, and more. Each article is carefully researched and reviewed to ensure quality and relevance.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Interviews
jack
I want to recommend this blog to my friends who what to grow their careers in the cyber security field.
Kyle Lee
Is it necessary to have a technical degree to start a career in cyber security and how to choose the best certification for a fresher level?
Aidan Johnson
Does janbask cyber security training would cover certification exam preparation?
Arlo Hill
Can you provide us some good sample of cybersecurity exam question pattern, is their any community you are associated with.
Brian Taylor
I have found various cybersecurity certifications, when i searched on google, how could i find the most valuable one or which one is more preferred by recruiters.
henry
Can you provide separate cybersecurity salary guide to explore there salaries in more details.
jemcy
What is course duration & total fee for cybersecurity training at janbask training.
ramcy
Very very thankful for such a nice written blog, i am looking for same information for last two months, gone threw so many blogs.