Introduction
Have you ever wondered how companies stay one step ahead of hackers? Or how someone with deep knowledge of hacking can actually build a legitimate, high-paying career?
That’s exactly what ethical hacking is all about.
Ethical hacking also known as white-hat hacking it is the art of legally breaking into systems to uncover weaknesses before the bad guys do. These professionals think like hackers, but act like protectors to help organizations prevent data breaches, financial loss, and reputation damage.
In a world where every click, tap and swipe leaves a digital footprint, cyber threats are no longer a distant concern they’re part of everyday life. Whether you’re worried about personal data being stolen, businesses collapsing from ransomware, or simply trying to build a career that feels future-proof, ethical hacking stands out as both a necessity and an opportunity.
But here’s the twist because not all hackers are the villains you see in movies. Some are the very reason your bank account is safe or your medical records aren’t leaked. Understanding the types of hackers is the first step to making sense of this digital battlefield.
In this article, we’ll guide you through:
- What ethical hacking really means
- The different types of hackers (and who the good guys really are)
- Why this field is more important than ever
- The career path, salaries, skills, and certifications you need to get started
Whether you're curious about the world of cybersecurity or seriously considering becoming an ethical hacker, this guide will help you connect and maybe even discover your next big career move.
Let’s dive in.
What is Ethical Hacking?
In this section, we will deal with “What is Ethical Hacking?”
Ethical hacking, often known as penetration testing, is the process of breaking into networks or computer systems to look for dangers or weaknesses that a malicious attacker might discover and use to steal data, cause financial loss, or cause other serious harm. By repairing the flaws discovered during testing, ethical hacking aims to increase the security of the network or system.

In order to increase security and protect systems from attacks by malicious users, ethical hackers are permitted to utilize the same techniques and tools as harmful hackers—but only with permission from the appropriate party. The penetration testing tutorial provides a quick glance at basic concepts of testing. Ethical hackers must notify management of any vulnerabilities and weaknesses discovered during the process.
Significance of Ethical Hacking
Today's most valuable asset for any company, is its "DATA," so protecting that asset should be the top concern for every company. The amount of data generated daily is enormous, whether we focus on government or private businesses. Therefore, there is a very high likelihood that cybercriminals, hackers, or even terrorist organizations may target their sensitive data. Organizations are taking preventive security steps to ensure their data is safe and secure because they are afraid of being hacked.

Regardless of the size of the company, firms worldwide must take proactive measures like updating security on a regular basis since hackers are constantly seeking new ways of different types of cybersecurity attacks to get past firewalls. White hat or ethical hackers have developed a new method of safety. They run pen tests to assess the organization's security precautions. Simply said, they break into the organization's networks and give full, in-depth information regarding the company's security posture. This raises their level of alertness and lowers the likelihood of actual threats like data theft by assisting the business in understanding the hacker's approach. We can also improve our security measures as we comprehend how a hacker might behave. All of this assures the business that the walls constructed for its data security are sufficiently thick and sturdy.
Before we move to the center of this blog and explore the types of hacking, you must know that going through this article will help you understand the different types of hacking and what ethical hacking is. But if you are looking to begin your career in this landscape, consider going for a professional Cybersecurity course.
What are the Types of Hackers?
Depending on how they intend to compromise a system, different sorts of hackers go by different names. There are primarily two types of hackers: White-Hat hackers and Black-Hat hackers. The names are inspired by vintage spaghetti westerns in which the excellent guy dons a white hat and the bad guy a black hat. Check below the list of different types of hackers

White Hat Hackers
White hat is one of the types of hacking that is legal and done with good intentions. To prevent this kind of hacking from happening to the data of a business, organization, or individual, permission is asked from the owner, and an investigation is conducted. White hat hacking is another name for ethical hacking, and those who engage in it are referred to as White hackers.
Analogous to black hat hackers, these types of hackers are cyber security experts who make use of their skills to identify vulnerabilities in business networks and computer devices. The significant difference among them is that white hackers are legitimate hackers who are permitted to hack networks or computer systems to identify security vulnerabilities before any hacker can.
Government organizations or large organizations often hire white hat hackers to identify and fix the vulnerabilities or weaknesses identified in business security systems to prevent data breaches or outer threats.
- The Motive of white hat hackers: To help organizations avoid cybersecurity threats
- Who’s highly at risk? - Criminal hackers
Black Hat Hackers
They hack in violation of the law, and they do so to further their financial interests. Black hat hacking is defended against ethical hacking. This type of hacking uses illegal techniques to penetrate a company's system or network or to breach security measures.
A black hat hacker is a hacktivist who gets access to computer devices with malevolent intent. These hackers execute their attacks using advanced technical skills and the ability to find their way in the cyber threat landscape.
They go the extra mile to identify the vulnerabilities in computer devices and software, which they utilize for capital gain or for different malicious activities. These black hat hackers can cause serious damage to individuals and businesses equally by credential theft or compromising complete systems or crucial networks.
- The motive of black hat hackers - To earn from data breaches.
- Who’s highly at risk? - These hackers are the most harmful to businesses.
Next, we will check about the grey hat hacker.
Grey Hat Hacker
A grey hat hacker works on the fusion of black hat and white hat hacking methods. The Grey hat type of hacking typically deals with issues of national security. Similar to the Black hat, this type of hacking is prohibited because it is done without the permission of the appropriate authorities.
Grey hackers, in contrast, don't break into any systems or networks for their profit or that of a third party. These hackers frequently break into a network or system to amuse themselves or to alert the owner to future security issues.
These types of hackers come with ways to hack into critical networks or computer systems, but without a malevolent intention of a black hat hacker.
- The motive of grey hat hacker: Personal enjoyment
- Who’s highly at risk? Everyone who declines unauthorized access to their computer systems and networks.
Script Kiddies
It is pretty evident that half knowledge is never safe. The Script Kiddies are amateur hackers who specialize in various aspects of hacking. Using programs created by other hackers, they attempt to compromise the system. They aim to breach networks, websites, or computer systems. Simply garnering recognition from their peers is the motivation behind the hacking. Script Kids are young people who don't fully understand the hacking process.
- The motive of script kiddies: To cause disturbance
- Who’s highly at risk?- Businesses and enterprises with unsecured networks and computer systems
Green Hat Hackers
Green hat hackers are those who are still learning the hacking ropes. Due to their purpose and involvement in types of hacking, they are a little different from the Script Kiddies. The goal is to work hard and gain the necessary skills to become expert hackers. Green hat hackers are looking for chances to pick the brains of seasoned hackers.
- The motive of green hat hackers: To learn how to become an experienced hacker
- Who’s highly at risk? - (Yet) No one
Blue Hat Hackers
Similar to Script Kids, Blue Hat Hackers are a subset of hackers. There is no desire to study. They employ hacking as a tool to acquire favor with other entities. To make amends with their enemies, they utilize hacking. Blue Hat hackers are counted among the hazardous types of hacking not because of their expertise but because of the motivation behind their hacking.
- The motive of blue hat hackers: To find out vulnerabilities in enterprise software before it gets released
- Who’s highly at risk? - Hactivists or Criminal hackers
Red Hat Hackers
Eagle-Eyed Hackers are often referred to as Red Hat Hackers. Personals involved in these types of hacking resemble white hackers. The goal of the red hat hackers is to thwart the black hat hackers' assault. The method of hacking through intention is the only distinction between red and white hat hackers. Red hat hackers are brutal when battling black hat hackers or using malware as a defense.

- The motive of red hat hackers: To identify and demolish black hat hackers
- Who’s highly at risk?- Black hat hackers
State/Nation Sponsored Hackers
Government agencies to use hackers to gather data on other nations. Professionals involved in these hacking types are called State- or nation-sponsored hackers. To be well-prepared for any potential threat to their country, they use their knowledge to gather sensitive information from other nations. Confidential information helps to stay on top of every issue while also helping to foresee potential risks. To their governments alone, do they report?
- The motive of state/nation sponsored hackers: To control and avoid international cyberthreats
- Who’s highly at risk?- International criminal hackers and criminals
Hacktivists
These types of hacking activities intend to hack government websites. They pose themselves as activists, so known as a hacktivist. Hacktivists can be an individual or a bunch of nameless hackers who intend to gain access to government websites and networks. The data from government files accessed are used for personal political or social gain.
- The motvie of hactivists: To throw light on dengerous social or political main cause (or to say something about a political or ideological situation)
- Who’s highly at risk? - Government organizations
Malicious insider or Whistleblower
Individuals working for an organization with access to sensitive information are among these types of hacking. The motivation behind the disclosure may be a personal vendetta against the organization, or the person may have learned of the unlawful acts taking place within the organization. The reason for it determines the purpose of the exposure. These people are referred to as whistleblowers.
- The motive of malicious insider or whistleblower: To reveal or leverage an organization’s sensitive or confidential information
- Who’s highly at risk? - Internal administration and top executives
The Bank Robber Hackers
These types of hackers aim to steal money from banks or other financial organizations. They either enter the network with the help of various tools and techniques. To target these institutions, they create dummy invoices, receipts, or DDoS attacks.
- The movie of the bank robber hackers: To steal money from banks or other financial institutions
- Who’s highly at risk? - Banks or other financial institutions without security measures
The Corporate Spy
These types of hackers, different from insiders, act on stealing either copyrights, trademarks, intellectual property, or another plan for personal or social gain. Mostly, they steal IP, financial and legal information, or confidential patents. Corporate spies might work for competitors or for other enemies to damage the business.
- The motive of the corporate spy: To steal intellectual property
- Who’s highly at risk? - Unsecured organizations
The Professional Hacking Group For Hire
The professional hacking group for hire work alone or in a group to build powerful and robust malware and then sell it for a reasonable price. They intend to earn finance or other valuable information. Individuals buying from them might further utilize them for abduction or secrete service.
- The motive of the professional hacking group for hire: To earn money
- Who’s highly at risk? - People who are targeted by the group
The Rogue Gamer
These types of hackers are the ones focused on gaming, who hacks systems to abduct competitors’ credit caches or damage their devices. It might sound foolish, but the rogue gamer does exist.
- The motive of rogue gamer: To deal with gaming competitors
- Who’s highly at risk? - Eminent gamers
Cryptojackers
These types of hackers target people who operate in cryptocurrencies. Cryptojackers transmit malware to their systems and steal their money by gaining the system's access. These hackers mostly do this to pay for the resources they use during hacking.

- The motive of cryptojackers: Cryptomining
- Who’s highly at risk?- Any person or enterprise with unsecured networks
The Botnet Masters
These types of hackers develop botnet armies and ultimately affect the system to gain control of it. The respective system then starts to work as per their instructions. Users mostly become their victims if they leave behind their credentials by default.
- The motive of botnet masters: To gain unauthorized access to extensive network systems
- Who’s highly at risk? - People with insecured routers and WiFi-connected systems
The Adware Spammer
These types of hackers act on annoying advertisements using viruses and other malware. These hackers redirect users to malicious websites and gain access to their systems using them. Adware spammers are extremely dangerous since a number of people ignore advertisements periodically.
- The motive of adware spammer: Gain unauthorized access to computer systems and crucial networks using viruses and/or malware
- Who’s highly at risk? - People who ignore advertisements regualrly.
The Thrill Hacker
These types of hackers wish to hack the system to experience the adventure of doing wrong. It’s more like they wish to set a standard for their abilities. Their motive is driven by popularity and image.
- The motive of thrill hacker: To experience the thrill of doing something wrong
- Who’s highly at risk? - Unsecured systems
The Accidental Hacker
These types of hackers aren’t really hackers. They’re more analogous to experts in the field who, by chance, end up hacking a website. They might do coding just for fun and experiments to check how it works.
- The movie of accidental hacker: To hack websites
- Who’s highly at risk? - Unsecured websites
These were the types of hacker attacks. Now, that we’ve seen how many types of hacker are there, In the next section, we will check the future of ethical types of hacking. Meanwhile, you can explore the JanBask Training for trending topics related to Cyber security courses.
Future of Ethical Hacking
Both the Internet and the e-commerce sector are constantly growing. According to research, internet users are significantly increasing, and businesses rely heavily on the Internet to operate. The risk of security breaches and data leakage is rising as more and more activities are conducted online. According to a recent KPMG poll across several industries, 72% of small- and medium-sized business (SMB) leaders reported being attacked by cybercriminals in the past year, up from 63% the previous year. Approximately 72% of the companies have experienced the same kind of cyberattacks in the past; of them, 78% lacked security mechanisms to stop the attacks. Hackers are developing new methods and tools to steal data in the present day.
Today's hackers are developing new ethical hacking tools and methods to break into organizations' databases and perhaps harm their enterprises. Because new types of hacker attacks strategies are frequently developing, therefore businesses need better plans, security precautions, and tools to thwart such attacks. As a result, there is a growing need for knowledgeable, ethical hackers. According to recent estimates based on industry research, 0.47 million ethical hackers are needed in India to defend the nation's IT infrastructure and the export market. This unmistakably shows that ethical hacking is highly beneficial and significant in the market and that it thus has a very promising future.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
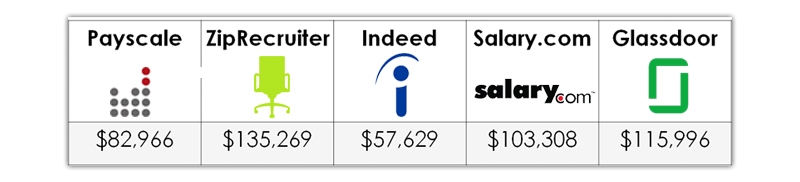
Salary Insights in Ethical Hacking
On average, an ethical hacker earns between $57,629 and $135,269, with an average payout of $99,034.
Because figures are sometimes changed in real-time based on changing data, cybersecurity salary estimates for cybersecurity occupations connected to ethical hacking vary widely depending on the methodology utilized. From reputable online career and cybersecurity websites, the following are some current ethical hacker income snapshots:

Top Career Paths in Ethical Hacking
A subset of cybersecurity is ethical hacking. Numerous employment options are available in this area as the types of ethical hacker attacks are improving. Following are some of the highest-paying positions you may pursue in this field.
An organization's digital security implementations are put to the test by an ethical hacker, who then recommends improvements based on the weaknesses found. They are specialists in breaking into networks to discover security flaws. Black-hat hackers take advantage of these flaws to compromise a company's cybersecurity system. In order to find and address any vulnerabilities, ethical hackers constantly audit the company's network security systems.
- Network Security Engineer
An organization's entire technology stack is handled and managed by a network security engineer. Engineers in network security provision, implement, configure, and manage a company's different network and security-related gear and software. They keep up virtual private networks, firewalls, and other security software. Additionally, they maintain the coding environment that safeguards servers, switches, and the company's IT infrastructure.
A cybersecurity analyst is in charge of guarding an organization against online dangers. They achieve this by utilizing a range of procedures and technological tools that identify and stop these dangers. It is the responsibility of cybersecurity analysts to evaluate how successfully their organization's security systems stand up to actual threats. They collaborate with other cybersecurity experts to fortify their organization's defenses against hackers and malware.
Hopefully, now you know the top job roles available in ethical types of hacking. For better insights into career options in hacking, check the complete Cybersecurity career path here!
How to Make a Career as Ethical Hacker
In the field of ethical hacking, hacking techniques are applied to benefit others and further a bigger cause. Here is a summary of how to begin a career in ethical hacking before going into more detail.

Step 1: Get Your Ethical Hacking Basics Clear
The first step in entering any domain is to educate yourself on the fundamental ideas involved. In regards to ethical hacking, the same is true. By taking advantage of these systems' and networks' current vulnerabilities, ethical hacking is a strategy for protecting system and network security.
Step 2: Learn about operating systems and programming
A profession in ethical hacking necessitates a solid understanding of programming languages due to the regular interaction with various systems. Additionally, you should be familiar with operating systems, including Windows, UNIX, LINUX, and IOS. Ethical hackers can spot programming flaws or faults by thoroughly understanding programming languages.
Step 3: Knowledge of Network and Security
A job in ethical hacking requires a solid grasp of cybersecurity and computer network fundamentals. For the goal of ethical hacking, there are a variety of publications, magazines, and online cyber security courses you may access online. You will be able to master computer security topics with the aid of these materials.
Step 4: Enroll in Training Programs and Earn Certification
Many training programs and free ethical hacking cyber security courses are being offered in the industry for hopefuls due to the rise in demand for skilled, ethical hackers. To improve your abilities and gain experience practicing ethical hacking in a real-world setting, you should enroll in a training program.
Before we move to the following sections, if you are serious about a career in ethical types of hacking, you must check out JanBask Training's Cyber Security Course or CISSP certification training course.
Skills Required to Become an Ethical Hacker
A wide range of abilities can help ethical hackers perform their jobs more effectively. Here's a rundown of the five in-demand skills:
- Software Development: Using their skills in software programming, ethical hackers create code to evaluate computer security. These occupations commonly employ programming languages like C and Python. In order to perform more effectively, they may also use database systems to track computer security information.
- Network Layout: Most ethical hackers are adept at creating networks that work for them. Constructing, maintaining, and troubleshooting computer networks of various sizes and types is possible. Knowledge of networking hardware, software, and security protocols, as well as an awareness of numerous network protocols, are prerequisites for this role.
- Communication: Writing and verbal communication skills are also necessary for careers in ethical hacking. A lot of ethical hackers communicate on the phone, by email, or in person. They might create code for computer security testing, work with team members, and hold meetings while using database systems to gather data.
- Research: Ethical hackers frequently conduct research to aid their business or customer in implementing security precautions. They might research the most recent hacking attacks and determine how to defend against them. They might use specialized equipment and software to study computer systems, which calls for knowledge of information technology.
- Problem-solving: Ethical hackers use their problem-solving skills to address complex security issues and spot security holes in modern technology and software. These skills also help them evaluate an organization's network or website security. Creating new software products might also help software engineers with problem-solving.
These were the top ethical hacking skills; now, let’s check the in-demand cybersecurity certifications you can take to succeed in your career.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
Top Ethical Hacking Certifications
If you're considering a career in ethical hacking, earning a certification is a great way to validate your skills and stand out in the cybersecurity job market. Here are some of the most respected and in-demand ethical hacking and cybersecurity certifications today:
- Certified Ethical Hacker (CEH) – by EC-Council: The CEH certification is one of the most recognized credentials in the ethical hacking field. It tests your knowledge of security threats, hacking techniques, tools, and countermeasures through both theoretical lessons and hands-on labs. Professionals with at least two years of experience in information security can take the exam directly, while others may opt for EC-Council’s official training program.
- Offensive Security Certified Professional (OSCP): The OSCP is known for its intensity and real-world applicability. Designed for technically skilled professionals, this certification demonstrates your ability to conduct advanced penetration testing using a practical, hands-on approach. A solid understanding of Linux systems, programming, networking, and exploit development is essential to succeed.
- GIAC Penetration Tester (GPEN): Offered by the SANS Institute, the GPEN certification verifies your ability to conduct targeted penetration tests and ethical hacking engagements. The program emphasizes both theoretical knowledge and hands-on practical skills, making it a strong choice for cybersecurity professionals who want to master offensive security.
- CompTIA Security+: While not solely focused on ethical hacking, Security+ is an excellent entry-level certification that covers a broad range of cybersecurity fundamentals, including network security, risk management, and cryptography. It’s a great starting point for anyone new to the cybersecurity field.
- Certified Information Systems Security Professional (CISSP): Ideal for experienced professionals, CISSP is a comprehensive certification that covers all aspects of cybersecurity, including security architecture, engineering, and management. While it’s broader than ethical hacking, it adds tremendous value to your resume and complements hands-on certifications like CEH or OSCP.
These are the top in-demand Cybersecurity certifications. If you wish to know about more certifications, you can check out more Cybersecurity certifications here! Now, let’s move to the following sections and know about the Ethical Hacker roles & responsibilities.
Role and Responsibilities of an Ethical Hacker
The purpose of ethical hacking is to examine a system or network's infrastructure security. An ethical hacker will attempt to circumvent system security to find and reveal any weaknesses that a malevolent hacker might exploit. Vulnerabilities are hardware or software mistakes typically discovered in insecure system settings. Hackers must get permission from the owner and receive their approval before examining the network and looking for security flaws.

Ethical hackers must carry out research, keep track of their findings, and communicate their findings to management and IT departments. Businesses and organizations utilize this information to improve their security measures in an effort to lessen or stop potential attacks. Ethical hackers will offer insight and confirmation to solve enterprise security problems. The information security industry has seen an increase in the popularity of ethical hacking. Implementing penetration tests is crucial for every business or organization that provides online services or is linked to the internet.
That’s it on the types of hacking, types of hacker attacks, career scope, earning potential, and in-demand skill sets and certifications. Think of joining the JanBask Training community to connect with industry experts and learn from their experience.
Conclusion
So, have you made up your mind to make a career in ethical hacking? Check out the certified ethical hacking training course at JanBask Training. It is a comprehensive training program that will guide you on what ethical hacking is, what the best practices used in hacking are, and how you can better protect your company from security breaches aside from advanced security and networking skills.
Frequently Asked Questions
Q. What is ethical hacking?
A permitted attempt to acquire unauthorized access to a computer system, application, or data constitutes ethical hacking. An ethical hack entails copying the tactics and behaviors of hostile attackers.
Q. What is an ethical hacking example?
For instance, logging into an email account to which you are not authorized, gaining access to a distant computer to which you are not authorized, and accessing data to which you are not authorized to have access are all examples of hacking.
Q. Is a career in ethical hacking worthwhile?
In light of the fact that it is one of the most significant ways to evaluate a network, ethical hacking is a worthwhile vocation. By trying various types of hacking, an ethical hacker seeks to identify weak spots there. By launching a brand-new assault that has never been attempted before, an ethical hacker can demonstrate to a firm where they might be exposed. The company can set up defenses to stop this form of intrusion once they have successfully entered the system.
Q. What is the ethical hacking salary?
Payscale reports that people with the Certified Ethical Hacker (CEH) accreditation make an average base salary of $82,966, which is over $3,000 higher than the national average for ethical hackers. For better insights, check the Cybersecurity salary guide now.
Q. Is a grey hat hacker good?
A grey hat hacker is someone who may transgress moral or ethical guidelines without having the evil intent associated with black hat hackers. A grey hat hacker may participate in actions that don't seem entirely legal, but they frequently work for the greater benefit.
Q. What is the motive of Green hat hackers?
Without the owners' permission, they often hunt for security issues and vulnerabilities in networks and software. Green hat hackers are mainly motivated by money and powder.
Q. How do you give a grey hat hacker definition?
The grey hat hacker definition can be given as grey hat types of hacking is the combination of black hat and white hat hacking tactics. Gray hat hackers frequently scan systems for vulnerabilities without the owner's knowledge or consent. If problems are discovered, they notify the owner and may occasionally demand a modest fee to have the issue resolved.
Q. What are the different types of hacking attacks?
These types of hacking attacks generally happen:
- Malware Attack
- Phishing Attack
- Password Attack
- Man-in-the-Middle Attack
- Injection Attack
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
6 days 30 Dec 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
5 days 29 Dec 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
2 days 26 Dec 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
2 days 26 Dec 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
2 days 26 Dec 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
3 days 27 Dec 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
-0 day 24 Dec 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
9 days 02 Jan 2026
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
10 days 03 Jan 2026
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
3 days 27 Dec 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
16 days 09 Jan 2026
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
5 days 29 Dec 2025






























Emerson King
What a nice descriptive blog post, covering everything about ethical hacking types, careers and their salary.
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Ronan Wright
I want to know, is there any separate course exist for ethical hacking career, what all skills are required to become ethical hacker.
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Karson Lopez
Well, this blog has covered so much about ethical hacking after reading this blog none of my doubt left about ethical hacking.
JanbaskTraining
Well, this blog has covered so much about ethical hacking after reading this blog none of my doubt left about ethical hacking.
Arlo Hill
Do you have a similar post covering ethical hacking tools that we can use for free and what is the career growth rate in ethical hacking.
JanbaskTraining
Do you have a similar post covering ethical hacking tools that we can use for free and what is the career growth rate in ethical hacking.
Tobias Scott
Ethical hacking professionals' demand is growing day by day as every organization wants to protect their network or system from cyber attacks so one thing is very clear that ethical hackers have secure careers.
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Brady Green
What salaries can they make? I wish I could switch to an Ethical hacker career and finally I want to thank the researcher for this post for providing such detailed information.
JanbaskTraining
What salaries can they make? I wish I could switch to an Ethical hacker career and finally I want to thank the researcher for this post for providing such detailed information.
Clayton Adams
I just want to know how to become an ethical hacking withoutwihtout any degree. Is it necessary to have coding language and if required what are all that?
JanbaskTraining
I just want to know how to become an ethical hacking withoutwihtout any degree. Is it necessary to have coding language and if required what are all that?
Francisco Baker
I love janbask blogs, they are always very informative plus full of interesting facts. Do you have any similar posts discussing Ethical hacker salaries and career paths?
JanbaskTraining
I love janbask blogs, they are always very informative plus full of interesting facts. Do you have any similar posts discussing Ethical hacker salaries and career paths?
Zander Gonzalez
Ethical hacker was a strange term for me, but today when I explored the Ethical hacker career, different profiles, and their salaries, I was just amazed, and many thanks for this well curated salary blog.
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Erick Nelson
How can I enter the Ethical hacker career, what are relevant courses and as I tried to find its certification, there were so many search results, how can I choose the best one?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!