Introduction
Cybercrime will cost the world $10.5 trillion annually by 2025, according to Cybercrime Magazine. In addition, the costs associated with cybercrime are expected to increase globally by about 15% annually in the next four years. Due to the pandemic, cryptocurrency and remote working have created a target-rich environment for criminals to take advantage of.
Top companies are willing to spend a lot of money on cyber security specialists who can safeguard company data and address breaches to defend against cyber attacks and security breaches.
You can take advantage of the situation and ensure a successful career in cyber security. Make sure you meet all requirements and possess the necessary qualifications and credentials. A specialized cyber security course can help you become an expert in this area.
So, if you are a beginner and need clarification on the importance of cybersecurity training and its future scope!
Down the post, you will get visibility on-
- What is cybersecurity?
- Why is cybersecurity training?
- Why cyber security training is important?
- Best cybersecurity practices
What is Cybersecurity?
Cybersecurity is the practice of safeguarding systems and sensitive information from digital attacks. Cybersecurity measures, also called information technology (IT) security, are intended to counter attacks on networked systems and applications, whether those threats come from within or outside an organization.

What is Cyber Security Training?
Cyber Security training is an approach to expand your understanding of the best techniques for protecting sensitive data. Training on cybersecurity awareness can go beyond the IT department and inspire coworkers on various teams to change how they access and use business data. Additionally, some businesses could make use of training to assist in the formulation of cybersecurity practices policies. Completing a training program in cyber security can help you manage digital information by completing a workshop or training course.
Hopefully, you get a clear picture of what is cybersecurity and what we learn in a cybersecurity course!
Now move on to the next section and explore why cyber security training is important for a career perspective and business growth!
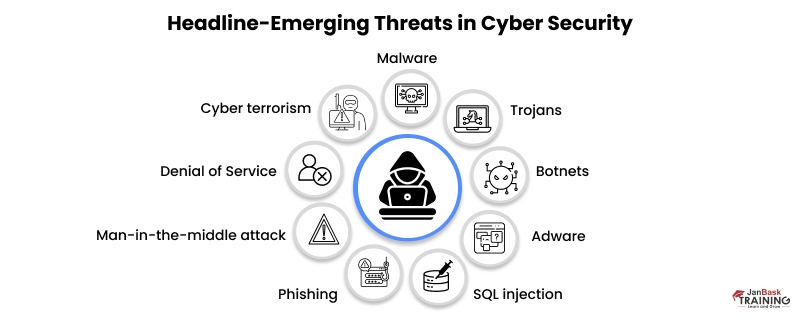
Types of Cyber Threats

We have established now that cybercrime refers to any unauthorized access to the system or network. And when it comes to types of cyber threats involved, cybercriminals have mastered the art of diverse styles. Let’s look at the usual cyber threats mentioned below:
- Cyber terrorism- It is a political attack on systems and information technology to impose harm and build massive social disturbance.
- Malware- This attack covers ransomware, spyware, and viruses. It can install dangerous software, block access to resources, disturb the system, and transfer data from the storage.
- Trojans- This attack manipulates users to think they are about to open a safe file. When the trojan is there, it enters the systems, creating a backdoor that facilitates access to hackers.
- Botnets- This attack includes massive cybercrimes by distantly managed virus-infected devices. You can think of it as a range of systems being a puppet in the hands of a hacker. Compromised systems emerge as a part of the botnet system.
- Adware- This is a form of malware. It is better known as advertisement-supported software. The adware virus is installed without permission and creates redundant advertisements.
- SQL injection- This cyber threat enters harmful code in the SQL-utilizing server.
- Phishing- Attackers deploy fake interactions, like e-mail, to manipulate the recipient into opening it. The user then follows the guidelines that demand sensitive details.
- Man-in-the-middle attack- This threat includes attackers entering a two-person online transaction process. The hackers can then filter and fetch the necessary information. Such threats occur on unsafe public networks.
- Denial of Service- This cyber threat pools the network with many handshake methods. It properly floods the system, making it inefficient in answering user requests.
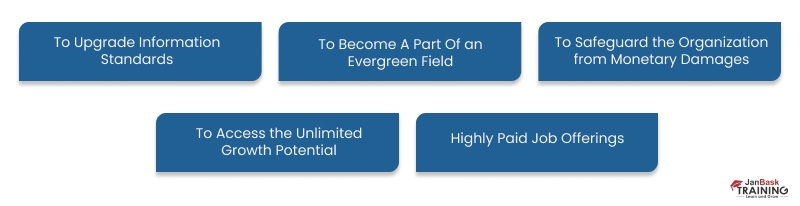
Why Cyber Security Training is Important – Explore the 5 Key Reasons

There has never been a better time to boost your knowledge of effective information security practices, whether you want to grow a business or a high-paying job. The importance of security awareness is rising with the highly evolving technological era. Today, the number of attackers is more significant than the count of users. Why is it important to learn about cybersecurity? Check out the reasons below to understand why cyber security is essential –
-
To Upgrade Information Security Standards: Currently, every firm is working to implement security policies and controls. Employees are informed about these regulations and how different frameworks and procedures interact through cybersecurity training. Another importance of Cyber Security programs is that it ensures employees are aware of the difficulties posed by security concerns and prepare them to handle any issues that may arise. On a larger scale, it assists employees in tracking security risks that emerge at their source and mitigating them before they worsen and develop.
-
To Become a Part of an Evergreen Field: An industry that will always be relevant is cybersecurity. The field of cybersecurity is both viable and sustainable. With the emergence of topics like big data, the internet of things, and cloud computing, the significance of cybersecurity has been firmly cemented in place. It is an important reason for cyber security courses and Cyber Security Certifications. In light of the importance of cybersecurity in the modern world, enrolling in a cybersecurity master's program is a magnificent option.
-
To Safeguard the Organization from Monetary Damages: Budgets for security are frequently created with software and AI in mind. However, there is one crucial aspect of cybersecurity planning that can have a huge impact on a company but is frequently disregarded – personnel. The finest security awareness training for employees increases the likelihood that they will quickly identify potential threats and report any subsequent events, it automatically increases the importance of cyber security and perfectly answers why cyber security training is important.
-
To Access the Unlimited Growth Potential: Cyberattacks are becoming more frequent and sophisticated these days – it alone can answer why cyber security training is important. Cybersecurity experts devote the majority of their time to outsmarting black hat hackers, patching vulnerabilities, and analyzing an organization's risk. In a constantly developing field, dealing with and preventing cyber threats requires ongoing study and in-depth research. Cyber security course is vital because it allows you to hone your wisdom and enrich your knowledge with experience.
-
Highly Paid Job Offerings: With headlines about new cyberattacks coming into the news every week, the world has come to understand the absolute necessity of cybersecurity. Businesses and governmental organizations are searching for professionals who can safeguard their systems from cybercriminals in the face of attacks online. They are prepared to pay high salaries and offer training and growth. Anyone interested in pursuing a career in cybersecurity has several excellent opportunities. The fact that cyber security salary has a higher growth potential than 90% of other businesses thoroughly explains why cyber security training is essential.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
If you are still wondering why is cybersecurity awareness important? The simple answer is stated here. The escalating number of technological tools has encouraged attackers to discover new ways to steal and tamper with the data. Hence, security awareness is vital to safeguard our systems from hackers. The point of security awareness's importance lies in the aspect of saving the system from malicious users.
The Subdomains Of Cyber Security
Cyber security covers technologies and methods to protect desktop systems, information, and networks from hackers. There are various subcategories of cyber security. Let’s have a look at them.
Application security
This encompasses using various protection within the firm’s software and services against multiple attacks. Application security calls for cyber security professionals to pen down proper code, create safe application frameworks, and use agile data input validation to evade the possibility of unauthorized access or change of application resources.
Cloud Security
Cloud security refers to producing safe cloud infrastructures and applications for agencies that deploy cloud service providers such as Amazon Web Services, Google, Azure, and others. This is also one of the subdomains of cyber security.
Identity management and data security
This subcategory encompasses tasks, structures, and methods that promote verifying and validating eligible people to the firm’s information systems. Such measures include utilizing potent data storage equipment that safeguards the data, irrespective of being in transition or staying on a computer. Also, data security uses verification protocols.
Mobile security
Mobile security is massive since most depend on mobile devices. Mobile security defends organizational and sensitive details stored on tablets, mobiles, and laptops from various attacks such as unauthorized access, viruses, and others. It also uses verification and education to support enhancing security.
Network security
Network security encompasses software and hardware mechanisms that defend the network from distortions, misuse, and various hacking efforts. Proper network security saves organizational resources from various threats in and out of the firm.
Disaster recovery and business continuity planning
This subdomain covers methods, alerts, observations, and strategies created to assist firms in keeping the business-crucial systems running smoothly after any massive event. Also, continuing lost tasks after the happening is executed in this subdomain.
User education
Knowledge is the ultimate weapon. Staff consciousness of cyber attacks is essential in the cyber security world. Providing staff training to businesses on computer security basics is vital to creating awareness about industry practices, organizational methods, and reporting malicious works. This subdomain caters to cyber-security-relevant classes and courses.

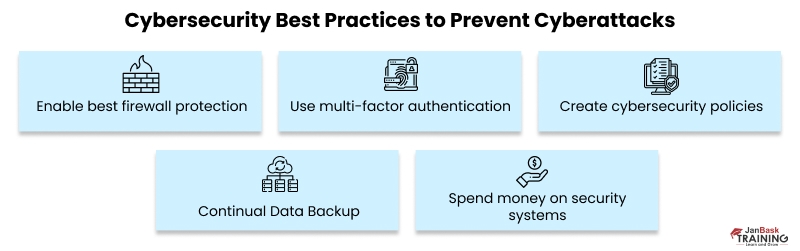
Cybersecurity Best Practices to Prevent Cyberattacks
Cybersecurity best practices encompass some effective tactics — from being cautious when engaging in online activities to abiding by company rules and reaching out for help when encountering something suspicious. Here is a deeper dive into the cybersecurity best practices to help protect your organization –
- Enable best firewall protection: The easiest strategy to fend against cyberattacks is to employ firewall protection for the company network, so be sure that it is enabled. The firewall stops unauthorized users from accessing their email accounts, websites, and other online data resources.
- Use multi-factor authentication: It helps protect your data by adding an extra layer of security that will make it harder for hackers to impersonate you. Even if a hacker manages to obtain your password, they would still need to pass a second or third authentication factor, such as a security code, one-time password, fingerprint, voice recognition, or other similar methods. You need to be a master in data security to grow on a Cybersecurity career path.
- Create the cybersecurity policies: A formal guideline for all cybersecurity measures gives a mechanism to implement the regulation that protects the data and enables the security professionals and the employees to be on the same line. However, each department's workflow is different and is susceptible to disruption from pointless measures. To increase the effectiveness of security measures that aid in thwarting malicious attacks.
- Continual Data Backup: The significance of data backup has grown in recent years. It is crucial to back up your data files and store them in a secure area following the company's security standards because cybercriminals frequently target your data. Data must be kept completely secure, encrypted, and updated regularly.
- Spend money on security systems: Small companies might avoid investing in high-quality security systems. Typically, this entails taking precautions like installing a powerful antivirus program, regularly scanning the system for malware, and using external hard drives to back up data. However, making that investment early could spare businesses and staff from the potential financial and legal repercussions of having their privacy violated.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
These are some of the best cyber security practices you must master. While you don’t necessarily need a degree to learn them, having accredited and structured cybersecurity training from a professional institute like JanBask Training can work great.

What Are The Significant Certifications For Cyber Security Experts?
A cybersecurity expert does not need to flaunt a conventional academic background. Hence, certifications have emerged as an industry-standard marker of authentic knowledge. This has also contributed to producing alternatives who wish to pursue a career in this domain.
Are you seeking professional guidance at a cheap rate? JanBask Training provides various certification-centered courses accessible to anybody, irrespective of their educational background. Let's look at some of the best cybersecurity certifications mentioned below:
Certified Ethical Hacking Certification (CEH)
Do you wish to know how to hack into systems? Then, this certification is the correct one for you. The Certified Ethical Hacking certification (CEH) will depict that ethical hacking capabilities can be a starting point for a great and exciting career path. This is one of the best cyber security certifications that solidifies your knowledge in the domain. It also indicates that the knowledge is authentic and verified.
CISSP Certification
This course will introduce you to everything you must know to become a Certified Information Systems Security professional. CISSP certification is the most demanding credential in today’s competitive job market. A little investment in this course can influence your career on a larger scale.
Job Roles And Salary Prospects Of Cybersecurity Experts
As organizations move towards answering the evolving cyber attacks, jobs in the cybersecurity domain are rising rapidly. Now, let's discover the various job roles and the respective salaries of cybersecurity professionals.
Entry-Level Cybersecurity Job Roles
Cybercrime Analyst- Cybercrime analysts earn an average salary of $100,000. The skills needed for this role involve computer forensics, information security, and malware engineering.
Cybersecurity Specialist- Cybersecurity specialists earn an average income of $104,482. The usual skills involve information security, information guarantee, and network security.
Incident and Intrusion Analyst- These professionals earn an average remuneration of $88,226. The common skills involve project management, intrusion identification, and network security.
IT Auditor- Also known as information technology auditors, these experts bring an average income of $110,000. The common skills involve internal auditing, audit strategizing, accounting, and risk handling.
Mid-Level Cybersecurity Job Roles
Now, let’s look at the job roles offered at the mid-level.
Cybersecurity Analyst- These cybersecurity experts earn an average of $107,500. The prime skills comprise information security, network security, and threat detection.
Cybersecurity Consultant- The cybersecurity consultants earn an average income of $92,504. The top skills in this job role comprise information security, resource protection, and security operations.
Penetration Tester- These cybersecurity experts earn an average income of $101,091. The capabilities needed include Java vulnerability assessment and software development.
Intermediate-Level Cybersecurity Job Roles
Finally, let’s look at the advanced-level job roles the cybersecurity field offers.
Cybersecurity Architect- Experts earn an average income of $159,752. The prime skills required involve software development and information security and verification.
Cybersecurity Engineer- Cybersecurity engineers earn an annual average salary of $117,510. The skills demand cryptography, verification, and network security potential.
Cybersecurity Manager- Cybersecurity managers get an average income of $130,000. Project management skills, knowledge of network security, and risk analysis must be one’s forte to become an expert in this field.

Conclusion
In this evolving cyber threat atmosphere, companies need well-qualified and skilled cyber professionals who can safeguard the web environment and help businesses stay ahead of the curve. As there is a huge demand for cyber professionals while the support is low, making your career in cyber security with an accredited cybersecurity training course can ensure a successful career for you.
Hopefully, you are now clear on why cybersecurity training is important. Have you found this post insightful? Do you have any confusion regarding the post? Let us know in the comments below!!
Frequently Asked Questions
Q1. Why is cybersecurity training and certification important?
Ans: Information security training, cybersecurity training, and certification are important because they protect a company from computer intrusions that expose sensitive data. The main goal is to prevent such occurrences, which can damage a brand's reputation and result in monetary losses and makes us realize security awareness importance. Hence, CEH training & certification is necessary to prove authentic knowledge in the domain.
Q2. How does cybersecurity affect your company?
Ans: Computers, servers, mobile devices, electronic systems, networks, and data are protected from hostile assaults, unauthorized access, and improper use by security measures. If you run a business, you need to make continuous efforts to secure your data from hackers by being cybersecurity-savvy. Protecting your computer from malware and viruses is important for preventing hazardous actors from accessing it.The CEH training & certification gives you the knowledge to protect the system from viruses and strengthen your knowledge on solid grounds.
Q3. What will cyber security look like in 2030?
Ans: According to Frost & Sullivan, over the next eight years, there will be a complex network of 200 billion connected gadgets on the planet, with over 20 devices per person on average. The IoT-connected gadgets' susceptibility to security vulnerabilities will increase as their capabilities advance.
Q4. Why cyber security training is important for the future also?
Ans: The internet, mobile computers, and electronic media have started taking over our work, personal, and financial lives. Unfortunately, this broad tendency leaves us more open than ever to fraudulent activity, privacy breaches, hostile attacks, and other bothersome things. To tackle these activities and safeguard important information, going through professional training can help you. That is why cyber security training is important for the future also.
Q5. What is the key factor in cyber security?
Ans: At present, the most critical factors in cybersecurity include visibility, mitigation, prioritizing, and encryption. Professional cybersecurity training courses can help you excel in cybersecurity. Also join the Janbask Training Community to connect, collaborate and learn more from Cybersecurity experts personally!
Q6. What does cybersecurity mean for a business?
Ans: Cybersecurity measures are focused on safeguarding computers, servers, mobile, electronic systems, networks, and data from malicious attacks and illegal access. To operate a business, make efforts to make yourself cybersecurity to keep your data protected from attackers. Anti-malware and antivirus protection is vital to keep dangerous elements out of your system.
Q7. Why is cyber security training important in the future?
Ans: The internet, mobile computers, and electronic media have started to take over our work lives, personal lives, and financial lives. Unfortunately, this broad tendency leaves us more open than ever to fraudulent activity, privacy breaches, hostile attacks, and other bothersome things. Hopefully, you are clear on why cybersecurity training is important.
Q8. What is the importance of information security training?
Ans: Training in security awareness helps to reduce risk, preventing the loss of PIN, intellectual property, money, or brand reputation. An efficient cybersecurity awareness program covers the errors that staff members may commit when utilizing email, the internet, and the real world, such as tailgating or incorrect document disposal.
Q9. What is information security training?
Ans: The information security training course covers a variety of crucial information security topics, such as how to recognize social engineering and phishing attacks, the importance of strong passwords, the use of social media, safe web browsing, and what to do when you suspect a data breach.
Q10. What are the benefits of the CISSP online training?
Ans: There are various advantages to opting for the online CISSP course. It will increase your earning capability and help you become a better candidate. Apart from creating cybersecurity professionalism, you can learn new concepts and apply them while working in the field.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
2 days 10 Jan 2026
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
2 days 10 Jan 2026
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
7 days 15 Jan 2026
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
1 day 09 Jan 2026
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 09 Jan 2026
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 16 Jan 2026
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
2 days 10 Jan 2026
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
2 days 10 Jan 2026
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 09 Jan 2026
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
9 days 17 Jan 2026
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
1 day 09 Jan 2026
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
2 days 10 Jan 2026



























raviraJPUT
Digital Marketing - Seo Diwana
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!
Kyle Lee
I want to know what the skills required to take up these cyber security courses and this post helped me in understanding well.
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Jax Williams
What a nice informative blog, a must-read for people who want to explore the best courses of cyber security.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!
Amari Jones
Hey, is there any separate guide that you can help me to get prepared for these certification courses?
JanbaskTraining
Glad you found this useful! For more such insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Zane Brown
Earlier I found that in a few places, the job opportunities after cyber security courses were not properly explained and after reading this post I got to know the different factors.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!
Emilio Davis
How to choose the best one among the cyber security courses mentioned above?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!
Knox Miller
Can anyone from a Science as well as commerce background join the cybersecurity training? If yes, then whom to contact?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!
Adonis Smith
I want to explore a few best courses for career growth, but confused about which one is better, I want to consult a JanBask consultant on this.
JanbaskTraining
Hey, thank you so much. We are grateful that our blog has been a help to you! For further insight do connect with us at https://www.janbasktraining.com/contact-us
Aidan Johnson
The insightful guide on Why Cyber Security Course Is Important is excellent. Please let me know a bit more about cyber security courses.
JanbaskTraining
Hey, thanks for sharing the feedback. We hope our blog has assisted you in making better decisions. For further assistance, you can connect to us at https://www.janbasktraining.com/contact-us
Kaden Brown
Excellent blog! I was confused about whether to pursue cyber security or not. But, after reading this blog I feel that cybersecurity is the right option for me. Thank you JanBask.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here and we will get back to you shortly!