How should I design an IAM role and attach policies for an app needing read-only S3 access?
I am an AWS cloud architect for a growing e-commerce company. My team Is developing a new application that requires read-only access to the S3 bucket for retrieving product images. However, I want to ensure that this Access is restricted only to the necessary bucket and doesn’t allow any modifications. How can I design an IAM role and attach policies to it so that I can meet these requirements efficiently and securely?
In the context of AWS, here are the steps given:-
Create an IAM role
You can use the AWS management console to create an IAM role. You can define the trust relationship for allowing service or entities to assume this role.
Create an IAM policy
You can create an IAM policy that can grant read-only access to the specific S3 bucket that contains product images.
Attach policy to IAM role
You can also attach the created policies to the IAM role that you created earlier.
Assign role to the applications
Finally, in your application’s code or Configuration, you can configure the AWS SDK or AWS CLI with the credentials of an IAM entity.
Here is the coding structure given for the above steps:-
Import boto3
Import json
# Create IAM Role
Iam_client = boto3.client(‘iam’)
Trust_policy = {
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Principal”: {
“Service”: “ec2.amazonaws.com” # Assuming your application runs on EC2
},
“Action”: “sts:AssumeRole”
}
]
}Trust_policy_json = json.dumps(trust_policy)
Role_response = iam_client.create_role(
RoleName=’ProductImagesRole’,
AssumeRolePolicyDocument=trust_policy_json
)
Role_arn = role_response[‘Role’][‘Arn’]
# Create IAM Policy
S3_policy = {
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Action”: [
“s3:GetObject”,
“s3:ListBucket”
],
“Resource”: [
“arn:aws:s3:::your-bucket-name”,
“arn:aws:s3:::your-bucket-name/*”
]
}
]
}S3_policy_json = json.dumps(s3_policy)
Policy_response = iam_client.create_policy(
PolicyName=’ProductImagesPolicy’,
PolicyDocument=s3_policy_json
)
Policy_arn = policy_response[‘Policy’][‘Arn’]
# Attach Policy to IAM Role
Iam_client.attach_role_policy(
RoleName=’ProductImagesRole’,
PolicyArn=policy_arn
)
# Assume IAM Role and Access S3
Sts_client = boto3.client(‘sts’)
Assumed_role = sts_client.assume_role(
RoleArn=role_arn,
RoleSessionName=’AssumedRoleSession’
)
S3_resource = boto3.resource(
‘s3’,
Aws_access_key_id=assumed_role[‘Credentials’][‘AccessKeyId’],
Aws_secret_access_key=assumed_role[‘Credentials’][‘SecretAccessKey’],
Aws_session_token=assumed_role[‘Credentials’][‘SessionToken’]
)
# Example: List objects in the S3 bucket
Bucket_name = ‘your-bucket-name’
Bucket = s3_resource.Bucket(bucket_name)
For obj in bucket.objects.all():
Print(obj.key)Hers is the example given by using HTML:-
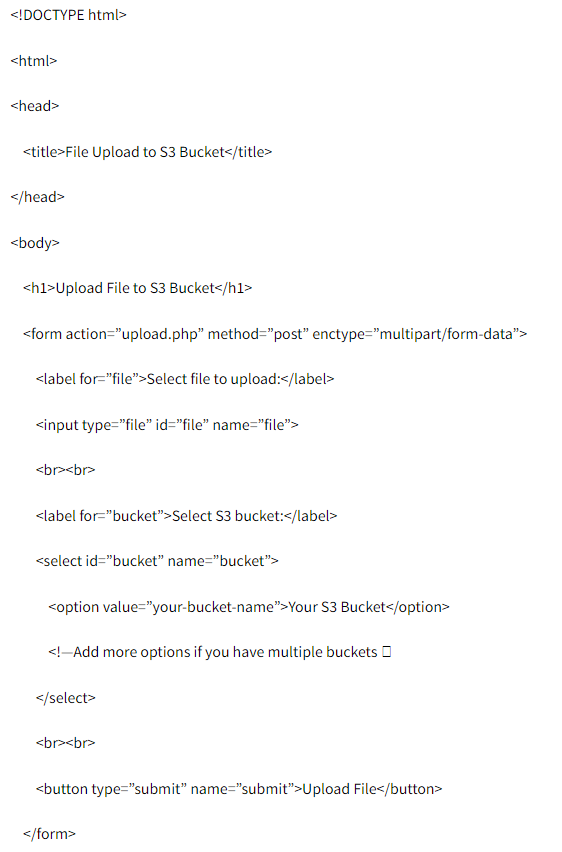
Here is the Python coding structure given:-
From flask import Flask, render_template, request, redirect, url_for
Import boto3
App = Flask(__name__)
# AWS credentials and bucket name
Aws_access_key_id = ‘your-access-key’
Aws_secret_access_key = ‘your-secret-key’
Bucket_name = ‘your-bucket-name’
# Create an S3 client
S3 = boto3.client(
‘s3’,
Aws_access_key_id=aws_access_key_id,
Aws_secret_access_key=aws_secret_access_key
)
@app.route(‘/’)
Def index():
Return render_template(‘index.html’)
@app.route(‘/upload’, methods=[‘POST’])
Def upload_file():
File = request.files[‘file’]
If file:
# Upload file to S3 bucket
Try:
S3.upload_fileobj(
File,
Bucket_name,
File.filename,
ExtraArgs={‘ACL’: ‘public-read’} # Set permissions as needed
)
Return redirect(url_for(‘index’))
Except Exception as e:
Return f’Error uploading file: {str€}’
Return redirect(url_for(‘index’))
If __name__ == ‘__main__’:
App.run(debug=True)

