How to troubleshoot and resolve "access denied" issue in an S3 bucket?
I am a cloud engineer and I am currently managing my company’s AWS resources. Recently, my team has noticed that there are some issues with accessing certain S3 buckets. Developers are reporting that they are receiving an error message stating that “access denied” when trying to read from or write to these buckets. How can I troubleshoot and resolve this particular issue?
In the context of AWS, here is the appropriate approach given:-
Verify the IAM policies
First, you would need to verify the IAM policies that are attached to the user or role. For this, you can navigate to the IAM console where you should select the user or role. Then there you can review the permission policies which are attached to ensure they include the necessary S3 action.
Review S3 bucket policies and ACLs
You should also check or verify the S3 bucket policies. For this, you can go to the S3 console where you have to select the bucket. Then navigate to the permission tab and review the bucket policies. You can also review the ACL setting under this permission tab.
Using cloud trail logs
Now you should check the cloud trail logs for the S3-related events. For this, you can open the cloud trail console and create or select an existing trail. Now you should search for the events that are related to S3 for identifying the potential issues.
Here is the example given in Java programming language:-
Add the following dependencies to your pom.xml files:-
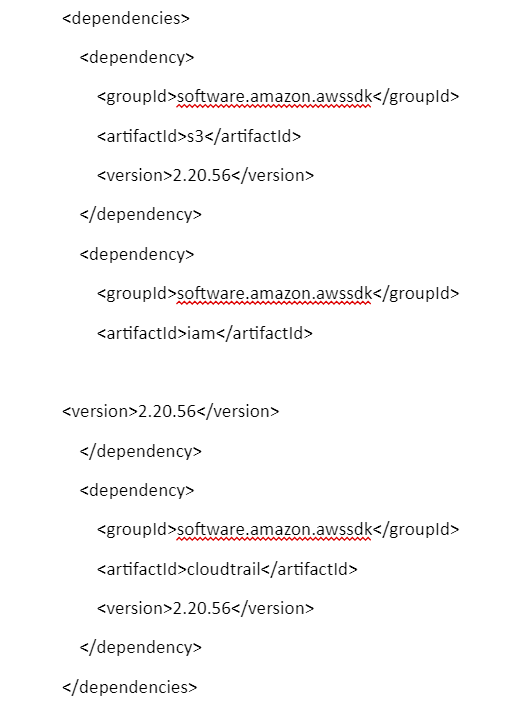
Now here is the java code given:-
Import software.amazon.awssdk.auth.credentials.ProfileCredentialsProvider;
Import software.amazon.awssdk.regions.Region;
Import software.amazon.awssdk.services.cloudtrail.CloudTrailClient;
Import software.amazon.awssdk.services.cloudtrail.model.LookupEventsRequest;
Import software.amazon.awssdk.services.cloudtrail.model.LookupEventsResponse;
Import software.amazon.awssdk.services.cloudtrail.model.LookupAttribute;
Import software.amazon.awssdk.services.iam.IamClient;
Import software.amazon.awssdk.services.iam.model.GetUserRequest;
Import software.amazon.awssdk.services.iam.model.GetUserResponse;
Import software.amazon.awssdk.services.iam.model.Policy;
Import software.amazon.awssdk.services.iam.model.PolicyDetail;
Import software.amazon.awssdk.services.iam.model.PolicyType;
Import software.amazon.awssdk.services.iam.model.Role;
Import software.amazon.awssdk.services.iam.model.RoleDetail;
Import software.amazon.awssdk.services.s3.S3Client;
Import software.amazon.awssdk.services.s3.model.BucketPolicy;
Import software.amazon.awssdk.services.s3.model.GetBucketPolicyRequest;
Import software.amazon.awssdk.services.s3.model.GetBucketPolicyResponse;Import java.util.List;
Public class S3AccessDeniedResolver {
Public static void main(String[] args) {
String bucketName = “example-bucket”;
String userName = “example-user”;
ProfileCredentialsProvider credentialsProvider = ProfileCredentialsProvider.create();
Region region = Region.US_EAST_1;
S3Client s3 = S3Client.builder().region(region).credentialsProvider(credentialsProvider).build();
IamClient iam = IamClient.builder().region(region).credentialsProvider(credentialsProvider).build();
CloudTrailClient cloudTrail = CloudTrailClient.builder().region(region).credentialsProvider(credentialsProvider).build();
Try { // Check IAM Policies checkIamPolicies(iam, userName);
// Review S3 Bucket Policies
reviewBucketPolicy(s3, bucketName);
// Lookup CloudTrail Logs
lookupCloudTrailEvents(cloudTrail, “GetObject”);
} catch (Exception e) {
e.printStackTrace();
} finally {
S3.close();
Iam.close();
cloudTrail.close();
}
}
Private static void checkIamPolicies(IamClient iam, String userName) {
GetUserRequest getUserRequest = GetUserRequest.builder().userName(userName).build();
GetUserResponse getUserResponse = iam.getUser(getUserRequest);
String userArn = getUserResponse.user().arn();
System.out.println(“User ARN: “ + userArn);
List policyDetails = iam.listAttachedUserPolicies(r -> r.userName(userName)).attachedPolicies();
For (PolicyDetail policyDetail : policyDetails) {
System.out.println(“Attached Policy: “ + policyDetail.policyName());
}
List roles = iam.listRoles().roles();
For (Role role : roles) {
If (role.assumeRolePolicyDocument().contains(userArn)) {
System.out.println(“Role assumed by user: “ + role.roleName());
List rolePolicies = iam.listRolePolicies(r -> r.roleName(role.roleName())).policyNames();
For (PolicyType rolePolicy : rolePolicies) {
System.out.println(“Role Policy: “ + rolePolicy);
}
}
}
}
Private static void reviewBucketPolicy(S3Client s3, String bucketName) {
GetBucketPolicyRequest policyRequest = GetBucketPolicyRequest.builder().bucket(bucketName).build();
GetBucketPolicyResponse policyResponse = s3.getBucketPolicy(policyRequest);
BucketPolicy bucketPolicy = policyResponse.policy();
System.out.println(“Bucket Policy for “ + bucketName + “: “ + bucketPolicy.policyText());
} Private static void lookupCloudTrailEvents(CloudTrailClient cloudTrail, String eventName) { LookupEventsRequest request = LookupEventsRequest.builder()
.lookupAttributes(LookupAttribute.builder().attributeKey(“EventName”).attributeValue(eventName).build())
.build();
LookupEventsResponse response = cloudTrail.lookupEvents(request);
Response.events().forEach(event -> {
System.out.println(“Event ID: “ + event.eventId());
System.out.println(“Event Name: “ + event.eventName());
System.out.println(“Event Time: “ + event.eventTime());
});
}
}
