 Year End Sale : Get Upto 50% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL
Year End Sale : Get Upto 50% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL

 Year End Sale : Get Upto 50% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL
Year End Sale : Get Upto 50% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL

Ans: You likely possess an object, such as a file or a database table, to which you intend to provide access. These objects, termed securables, serve as the resources that the authorization system governs access to. Certain securables might be nested within others, forming hierarchical scopes known as scopes, which can be secured. The SQL Server Database Engine encompasses three secure scopes: server, database, and schema. Each securable within SQL Server is accompanied by associated permissions that can be granted to a principal.

Ans: This login can include a custom username (e.g., Login1) and a robust password. Alternatively, you can employ an existing Windows account to access SQL Server, obviating the need for a new username and password. This categorizes SQL Server logins into two types: Windows logins and SQL Server logins. Logins do not automatically possess access to specific databases within SQL Server; their purpose lies in enabling connection to a SQL Server instance. As such, logins are entities eligible to receive server-wide permissions for carrying out specific actions. These tasks are grouped within server roles like sysadmin, diskadmin, and dbcreator, among others. To delve deeper, consider pursuing Online SQL certifications.
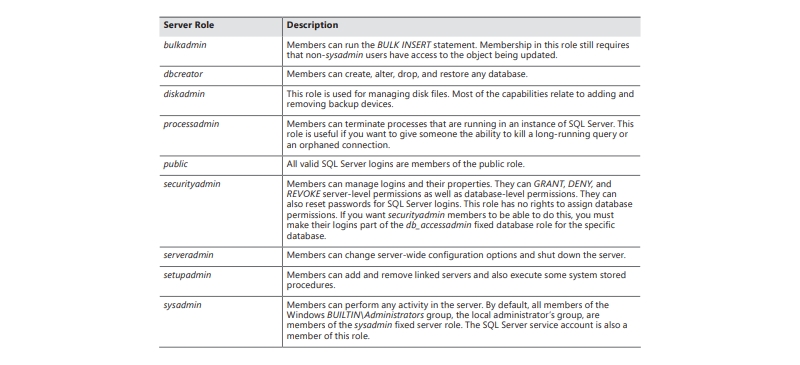
Ans: Table 5-1 provides an inventory of server roles alongside their associated functions. Server roles are predefined and cannot be altered—no new roles can be added to the existing nine fixed server roles.
Ans: To create logins, SQL Server Management Studio (SSMS) or the Transact-SQL (T-SQL) statement CREATE LOGIN can be utilized. Following login creation, you can extend access to a specific database. Databases are equipped with distinct sets of roles that delineate specific access rights and actions for users with these roles within a database. Before bestowing database access upon a login, it's imperative to first establish a database user for the login. The creation of a database user can be executed through SSMS or the T-SQL statement CREATE USER.
Ans: When generating a database user, the option exists to add them to one of the predefined database roles.Expounds upon the roles integral to all databases. Comparable to server roles, these database roles are static and resistant to alteration. In contrast to server roles, the creation of supplementary database roles is feasible.
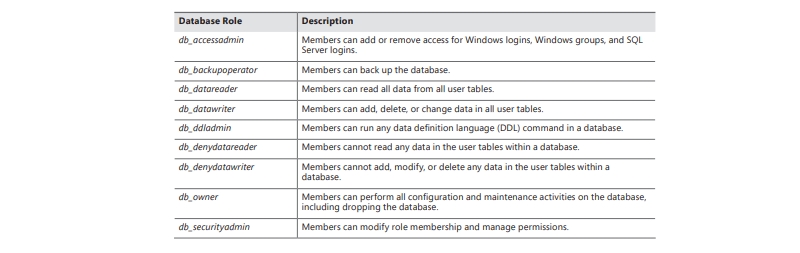
Ans: The public role is an exceptional database role that sysadmin users cannot directly authorize for other users. Implicitly, the public role is assigned to all database users. This role encompasses default permissions for users within a particular database. However, it cannot be allocated to users, groups, or roles, as every individual is automatically part of this role. The public role is irremovable. Therefore, to curtail unauthorized data access, it is recommended to restrict permissions assigned to the public role, while channeling permissions through other database roles and user accounts associated with logins. For deeper insights, exploring Online SQL certifications is beneficial.
Ans: Regarding unauthorized data access, it is noteworthy that SQL Server accommodates a unique user account termed "guest." This account is automatically generated within new user-defined databases, and it also exists in master and tempdb databases. The guest account, however, is disabled by default, rendering it devoid of database access. The guest account permits entry into a database without necessitating a dedicated user account.
Ans: A login assumes the identity of the guest account when the following criteria align
Ans: Permissions can be granted to the guest account similarly to any other user account. It's advisable to minimize reliance on the guest account, as logins lacking specific database permissions inherit permissions allocated to the guest account. If utilization of the guest account is imperative, ensuring it maintains only essential permissions is crucial.
Ans: Previous iterations of SQL Server facilitated client connections via protocols like TCP, named pipes, shared memory, and VIA. As long as one of these protocols was enabled on the server and the user possessed a valid login, connection was feasible. SQL Server 2005 introduced endpoints to compartmentalize this functionality. Endpoints serve as gateways to access SQL Server.
Ans: Administrators can configure endpoints for TCP, named pipes, shared memory, VIA, and even HTTP. Upon establishing an endpoint, access can be restricted to specific endpoint types exclusively. For instance, a login named Login1 can be granted access solely through the HTTP endpoint, while other endpoints remain inaccessible. Delving into the process of client connection elucidates how this endpoint validation influences authentication. For a more thorough grasp, consider embarking on an Online SQL certification course.
By engaging with this content and its insights, you've taken the first step toward building a robust security foundation for your SQL Server environment. Remember that each topic covered here can be explored in greater depth, making continued learning and practice essential for mastering SQL Server security. As the digital landscape evolves, ongoing education, perhaps through online SQL certifications, will empower you to stay at the forefront of security best practices and effectively protect your valuable data assets.

SQL Server MERGE Statement: Question and Answer

Top SSRS Interview Questions And Answers


Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Download Syllabus
Get Complete Course Syllabus
Enroll For Demo Class
It will take less than a minute
Tutorials
Interviews
You must be logged in to post a comment