Christmas Offer : Get Flat 35% OFF on Live Classes + $999 Worth of Study Material FREE! - SCHEDULE CALL
Today, many people are talking about the impact of information technology on the world. They discuss how business, economics, education and even personal relationships are affected by the advent of the information age. Thus, you’re required to learn cyber security skills and techniques to defend against cyber threats and secure your critical information through cybersecurity courses. The term "information warfare" has been used for many years to describe what warfare looks like in the information centric century. In an effort to move forward towards a common definition, this blog introduces and expands on one possibility by discussing the weapons and strategies involved in defined "information warfare".
Everyone knows about wars. They are as old as our myths and legends. There are different types of warfare, from using traditional warfare to chemical and biological warfare, humans have tried to create havoc and establish their superiority over his fellow men. The ultimate goal of any warfare is to win over the adversary using any tactics possible. Information warfare is no different. Using information to their advantage, the attacker can manipulate information trusted by a target without the target's knowledge so that the target will make decisions against their interest but in the interest of the one conducting information warfare.
The unique feature of information warfare is that it is hard to exactly say when the attack begins and ends. It is also hard to determine the damage it causes. Information warfare usually includes a collection of strategic information, giving assurance that the information is valid, propagating false information, demoralizing the target, and for spreading propaganda. In a way, information warfare is related to psychological warfare as it includes using the information to degrade the quality of the information of the target and preventing true information from their reach. We have seen this in the recent Russia vs Ukraine war.
Information warfare can happen anywhere. From countries to corporations and even individuals can be targets of information warfare. There are agencies and governments that take interest in this mode of warfare and are actively involved in them. Information warfare examples include third-party interference in elections happening over the world, spreading fake news etc. Many people link information technology with programmers or else with after-sales service professionals. But you'll be surprised to know that its just a shallow definition! Remember that everyone has a place in the IT world, and if you wish to break into this field, go through our comprehensive guide on IT career path.
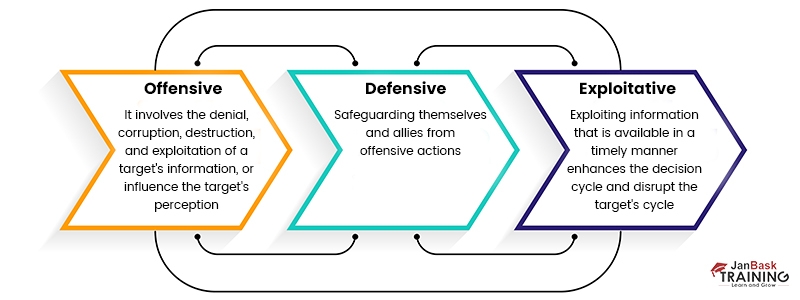
The goal of information warfare is to have information superiority. It is termed as the ability to collect, process, and disseminate information more efficiently or effectively than the adversary. Information warfare can be divided into three categories: offensive, defensive, and exploitative.
The fact that information technology is increasingly becoming more relevant to the lives of common person’s lives means that those who indulge in information warfare are not just armies and soldiers. It means that anybody who understands computers may become a “fighter” or a “soldier” on the network. The rapid development of networks and the internet of things has turned each automated system into a potential target of invasion when it comes to information warfare in the cyber world.
Cyber warfare is information warfare in the cyber world. In a world run by automated systems and computers, the damage it can cause is rather immense. Countries like Russia, China, America, and North Korea are said to have their own cyber armies trying to get into people's data all across the world. Think tanks composed of non-governmental experts may take part in decision-making. Influencing common people during times like elections has the potential to change the power structure of an entire country. In the 2010s, British consulting firm Cambridge Analytica collected personal data from millions of Facebook users without their consent, primarily for use in political advertising.
The majority of the time, nation-states engage in cyber warfare by attacking other nations, but occasionally, terrorist groups or non-state actors carry out the assaults to further the objectives of an adversary state. There have been many reported instances of cyber warfare in recent years, but there is no established definition of what constitutes an act of war in the context of a cyber-strike.
This refers to spying on other nations in order to steal their secrets. In terms of cyber warfare, this can entail compromising delicate computer systems employing spear phishing or botnet operations before leaking sensitive data.
Governmental entities need to assess the risks associated with compromised sensitive information. Terrorists or hostile countries may steal information, destroy it, or use internal threats like unhappy or negligent employees, or government workers with ties to the attacking country.
DoS attacks stop legitimate users from using a website by bombarding it with fictitious requests and making it respond to them. Critical activities and systems can be interfered with, and sensitive websites can be made inaccessible to people, members of the armed forces and security forces, or research organizations. Go through a tutorial on performing DDoS attacks to get answers to all your questions on DDoS attacks.
This includes attempts to influence the ideas and thoughts of individuals who are residing in or supporting a target country. Propaganda can be used to reveal embarrassing facts, promote falsehoods to undermine public confidence in a government or support one's adversaries.
Computers are used to run the majority of current economic systems. Attackers can attack the computer networks of commercial institutions like banks, payment systems, and stock exchanges to steal money or prevent individuals from getting the money they require.
The need to restrict your opponent's access to information is one of the information warfare strategies on which everyone agrees. Preventing the opposite side from stealing your information is a big component of this. There are two categories of weapons employed to safeguard the security of our information. Our most important data storage facilities, computers, and transport systems are first protected by technology like bomb and bulletproof casings, as well as intrusion prevention systems like locks and fingerprint scanners. Technologies that prevent bits from being viewed and intercepted by the opponent are second, and possibly more crucial. This certainly includes simpler computer security mechanisms (such as passwords) and more complex technologies (such as encryption).
There are several ways, many of which employ the same techniques that are used in attacks.To defend against information collection attacks is to prevent our enemies from assembling information about us and about the conflict situation, and to prevent them from information manipulation.

Cyber Security Training
From this discussion, information warfare is no less complex than traditional warfare. It involves many different strategies, techniques, weapons, and defenses.
Enroll in the cybersecurity courses by Janbask training to learn more about it.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Download Syllabus
Get Complete Course Syllabus
Enroll For Demo Class
It will take less than a minute
Tutorials
Interviews
You must be logged in to post a comment