Grab Deal : Upto 30% off on live classes + 2 free self-paced courses - SCHEDULE CALL
With the advancement of science and modern technology, human intelligence has also taken a curved evolution. Human life has become much more sophisticated and well fascinated with wide expansion of internet connectivity through various modes of devices. But whenever we feel the soothing benefits of internet and computer networks a huge question mark of its theft and further protection comes to mind. With the huge growth and expansion of internet and computer connectivity in the cyber world, the question of its protection from illegal handling also creates a common question mark.
In order to protect all of our crucial and private information, cyber security plays a major role in our society. Before protecting our online information and credentials, we should understand how various threats and attacks could happen in the cyber world. For that, we must first learn cybersecurity by enrolling in cybersecurity courses. Here the concept of the Attack vector comes in.
Attack vector in cyber security is the process or method of obtaining unauthorized access to launch a cyber-attack. Cyber criminals utilize numerous illegal and unlawful actor vectors to breach the valuable data of target individuals or organizations and exploit their system vulnerabilities. Attackers take advantage of sensitive and weak systems and try to preach through individuals biometrics, personal details, and so on. This vector may include malware, email attachments, instant messages, web links, and so on.
Such cyber security attack vectors are directly or indirectly motivated by various factors. It may be religiously motivated to create havoc among certain community, financially motivated to steal money or other valuable documents and data, socially motivated to publicize certain private and secret information by terrorists, political workers or rival state sponsored groups to embrace specific organizations.
Cybersecurity attack vectors are the pathways to gain access to unlawful and illegal credentials and sensitive data without the consent of the individual.
However, Attack surface is the total number of attack vectors utilized to breach the data, steal system credentials, and launch cyber-attack.
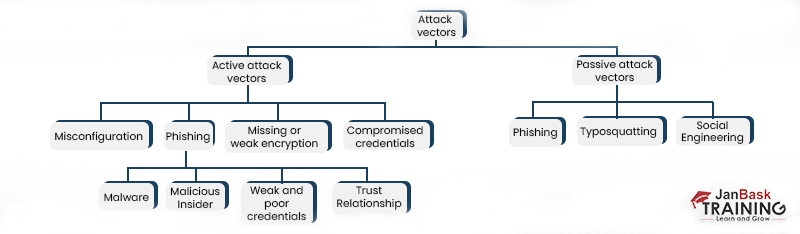
There are various ways to alter, disable, destroy or steal very crucial information through unauthorized access.
In general, we can classify cyber attack vectors as passive or active vectors.
In this method, a hijacker may damage or destroy the target individual or organization system resource or operation system. It may include phishing attack, man-in-the-middle attack, Denial of service etc.
One of the most common illustrations for such an attack is masquerade attack, where a hijacker pretends to be a legitimate and trusted source user and tries to steal login credentials to obtain system resources unethically.
In such attacks, cybercriminals try to monetize system vulnerabilities to gather information about target sources. Many of the times such attacks are difficult to detect as no suspected alteration or damage of the source system is involved.
It may include phishing, typosquatting, and other social engineering attacks. Click here to get a list of malicious websites, that might be involved in phishing, scams, viri, or other malware.
In the wide exposed cyber world, it is the responsibility of any user to understand and identify the possible cyber attack vectors in order to protect his or her system risk free.
Most common way to protect one's private and crucial data is username and password. In many cases username and weak passwords are leaked and exposed to attackers through unsuspected web browser, messages and email activities. It happens when unaware online users unknowingly fall prey in phishing attacks and enter login credentials in fake websites and links. If an attacker gets access to privileged credentials then it poses a very high risk and complications to resolve on time.
Ways to avoid
Trust relationship defines a level of trust between two systems or domains to keep the information safe and easy to access without asking for multiple login. In this type, the user system has to login only once, which will be valid for a longer period. Any breach in the trusted domain may lead to exposing users’ sensitive data with vulnerabilities.
Any error in configuration leads to misconfiguration. If the default username and password is not disabled in an application, then hackers may get access to hidden data, credentials, and lead to obtain extra information.
Phishing is one of the widely used social engineering attack vectors that are imposed through email attachments, telephone or text messages by pretending to be a trustworthy institution which seeks to access very sensitive data such as personally identifiable information, Healthcare, banking and card details and login details.
Encryption converts clear text to ciphertext. Encryption ensures safety of confidential data in computer systems. Any type of weak and missing encryption may create a loophole for users, which could be an advantage for cybercriminals to get unlawful access.
A malicious insider is a type of employee who reveals or exposes confidential data or exploits company vulnerabilities. These employees are the unhappy and dissatisfied employees of the company who ultimately want to damage the company from all directions.
Malware contains numerous malicious software such as ransomware, spyware, Trojans and viruses. Cybersecurity attackers use such devastating software as threat vector to steal or publicize data of various computer systems and networks.
Use advanced technology like firewall, antivirus, anti-malware, sandbox chrome, etc. to detect and block unusable sites and attacks. Explore more about what sandbox chrome means, here.
Using the same weak password across different platforms can lead to compromised credentials and further attacks.

Cyber Security Training
With the advancement of the 21st century, many types of unprecedented and unexpected cyber threats have created question marks for safe online use. Therefore, understanding and identifying appropriate attack vectors are very important in the current situation. Correct trust relationships and resilient cyber security posture may eliminate or reduce cyber vulnerabilities. Similarly, managing and monitoring each and every digital application in your computer system is essential. Above all creating social and digital awareness through various campaigns, and programs can be a matter of public benefit to detect and get rid of such risks.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Download Syllabus
Get Complete Course Syllabus
Enroll For Demo Class
It will take less than a minute
Tutorials
Interviews
You must be logged in to post a comment